3 Tips For Choosing The Best Vehicle Access Control Gates
10 Tips to Help Homeowners Choose the Right Access Control Systems
In addition, a deal record of all DFO and OTL conditions is sent to the access control server computer system for storage. The deal record shows the name of the door at which the condition took place, the type of event that occurred (DFO or OTL), and the time that the condition happened.
The access control software enables Mary to define the time durations during which the DFO and OTL monitoring functions will be in effect For example, Mary may choose that it would be O.K. for the back door of the Administration Structure to be propped open throughout routine working hours (8:00 A.M.
 10 Tips for Parking Access Control Software
10 Tips for Parking Access Control SoftwareMary does not desire the back door to be propped open at any time other than routine working hours. To accomplish this, Mary sits at the access control server computer system and enters the time durations during which she does desire DFO and OTL monitoring functions to be in impact; in this case, 5:00 P.M.
The collection of these saved transactions is called the "system journal". The system journal is just a computer database in which records of gain access to control deals are saved. There are various types of gain access to control system transactions. Some of the more common types of transactions include: Valid Access: A entry through a door using a legitimate gain access to card.
Tips For Choosing a Commercial Access Control Software
The gain access to control system allows the production of reports of different types of system deals. These reports are created at the gain access to control server computer; and might be shown on screen, or printed on a computer printer. Reports can be produced based on a set of parameters specified by the individual managing the access control system - face recognition access control.
Day-To-Day Operations The following are some everyday operations that Mary Simpson, as manager of the access control system at the Administration Building, is likely to experience: Card Does not Work Circumstance: Susan Bright attempts to use her card to enter into the computer room this Wednesday. Her card does not enable access into the computer system space as it should.
Access Control by Fresh USA
Address: 9 Mc Gregor Ct, Hawthorn Woods, IL 60047Phone: +1 (312) 312-9608
Email: order@fresh222.com
Click here to learn more about Access Control
Access Control by Fresh USA
9 Mc Gregor Ct, Hawthorn Woods, IL 60047+1 (312) 312-9608
Click here learn more about Access Control
This is the very first time that Susan has tried to use her card at the computer room door given that the gain access to control system was installed. Susan informs Mary that her card does not work. Action: Mary checks the clearance code designated to the card, and finds that she inadvertently assigned the wrong code.
 Hiring a Parking Access Control Software
Hiring a Parking Access Control SoftwareAction: Mary issues Brian a new gain access to card. Mary finds that she does not have a clearance code that corresponds to Brian's access benefits, so she creates one, and after that assigns it to Brian's card. Employee Ended Scenario: A janitorial employee, Steve Woods, has actually been terminated. The agreement janitorial company notifies Mary that Steve has been terminated, but that he has not yet returned his Administration Building gain access to card.
Advice on choosing a Parking Access Control Software
Change of Auto-Unlock Time Circumstance: The management of the Administration Building chooses that the front door of the building ought to open to the general public at 7:00 A.M., rather than at 8:00 A.M. as it presently does. Action: Mary redefines the automatic unlock time setting for the front door to 7:00 A.M.
It will take 24 hr for the new flooring finish to dry. The structure management has alerted all workers not to get in the building this weekend, but hesitates that some staff members might forget and be available in anyhow. Action: Mary sets the access control system to momentarily disable the access advantages of all staff members (except custodial workers) till Monday early morning - entry and exit access control systems.
John asks Mary to create a gain access to report. Action: Mary utilizes the access control report function to print out a report of all persons who entered the computer system room last Saturday.
A few of these optional features include: Automatically-Locked Doors In some cases, it might be preferable to lock and unlock doors automatically. This is often done on buildings which are open to the general public during the day, however are closed at night. In these cases, automated locking and unlocking removes the need for a person to perform this function by hand.
Avoid These 3 Mistakes When Choosing a Temperature Access Control
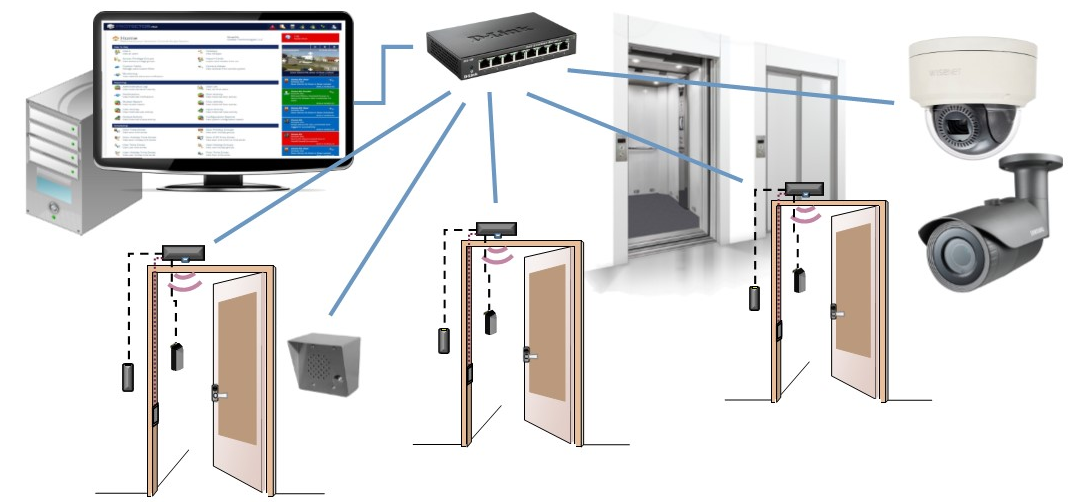 6 Tips for Finding The Right Access Control Software
6 Tips for Finding The Right Access Control Software
In many cases nevertheless, the structure management may wish to immediately lock and unlock doors that are not geared up with a card reader. Doors which lock and open instantly but which do not have a card reader are called "Automatically Locked" doors. Automatically locked doors can be set to lock and open at particular times similar to card reader controlled doors can - car parking access control.
 Tips For Finding The Best Commercial Parking Access Control System
Tips For Finding The Best Commercial Parking Access Control System
Typically, automatically locked doors are used in conjunction with card reader doors. For instance, in numerous buildings, there are four doors at each building entrance. To allow night entryway, among these four doors is equipped with a card reader. The other three doors are equipped with electric lock hardware to allow them to be automatically locked.
Instantly locked doors normally likewise provide the "Door-Open-Too-Long" (OTL) tracking feature to prevent them from being propped open. Monitored Doors In many cases, it is preferable to have door status tracking on doors which are not card reader controlled and not automatically locked. vehicle access control systems. A door that is connected to the access control system for monitoring purposes just is called a "monitored door".
When a monitored door is opened, it reports to the gain access to control system server computer system - access control for parking lot. The actions to be taken when the door is opened can vary depending upon how the system has been configured. At the Administration Structure, there is a door that leads to the roofing system.
Choosing a Professional Face Recognition Access Control
Mary arranges to have this door monitored by the access control system. When the door to the roofing is opened, it sounds an alert at the access control system server computer, alerting Mary. In addition, the event is taped on the system journal at the server computer enabling future recall through the reporting feature.
