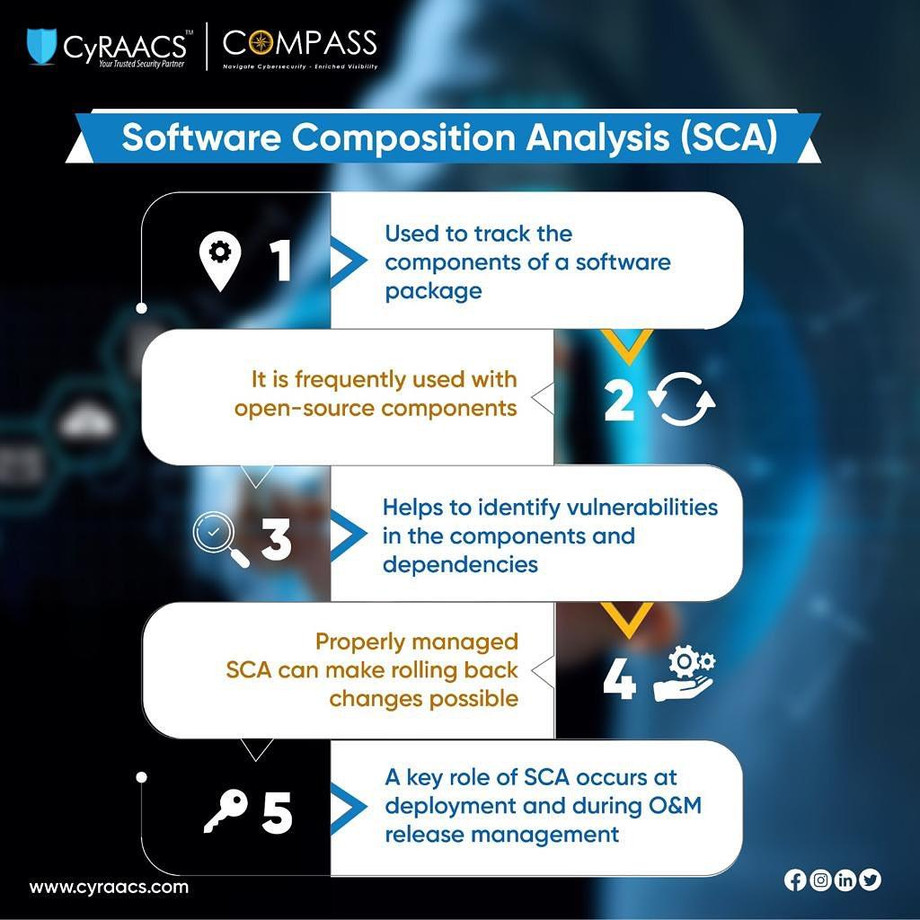
SCA goes beyond traditional code analysis, scrutinizing the third-party components and open-source libraries that make up a software application. With cyber threats on the rise, understanding and managing the vulnerabilities within these components is crucial. Reach out to CyRAACS™ at www.cyraacs.com to know more.