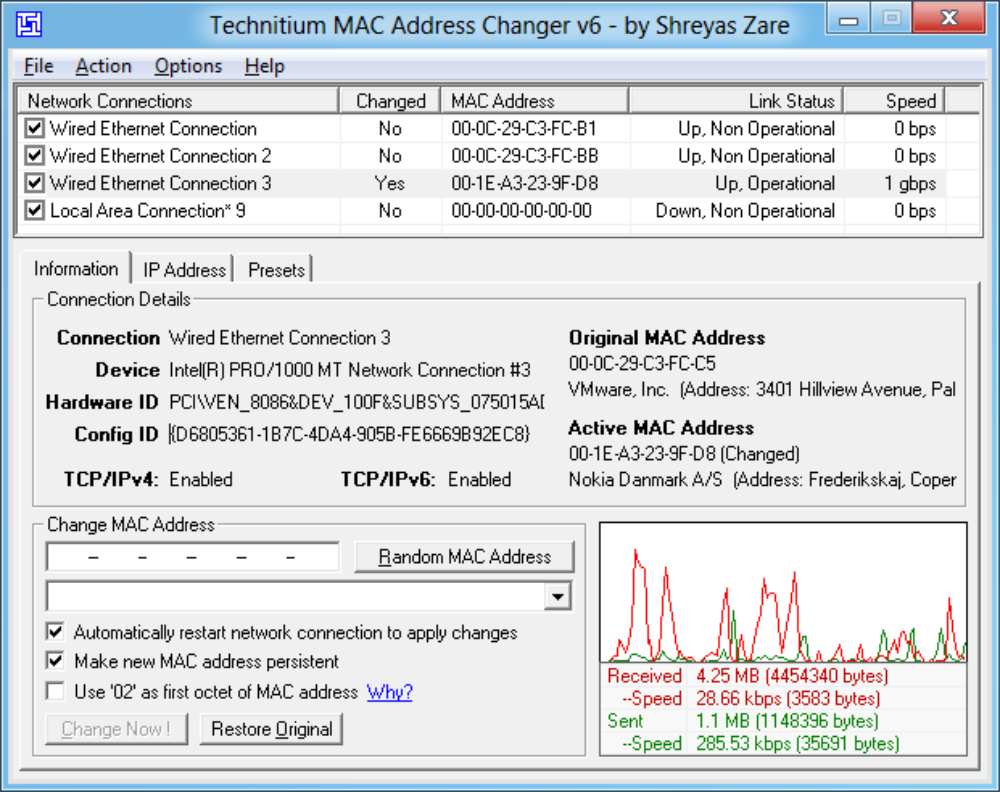
This is a detailed tutorial of how to do a man-in-the-middle attack on a bank.

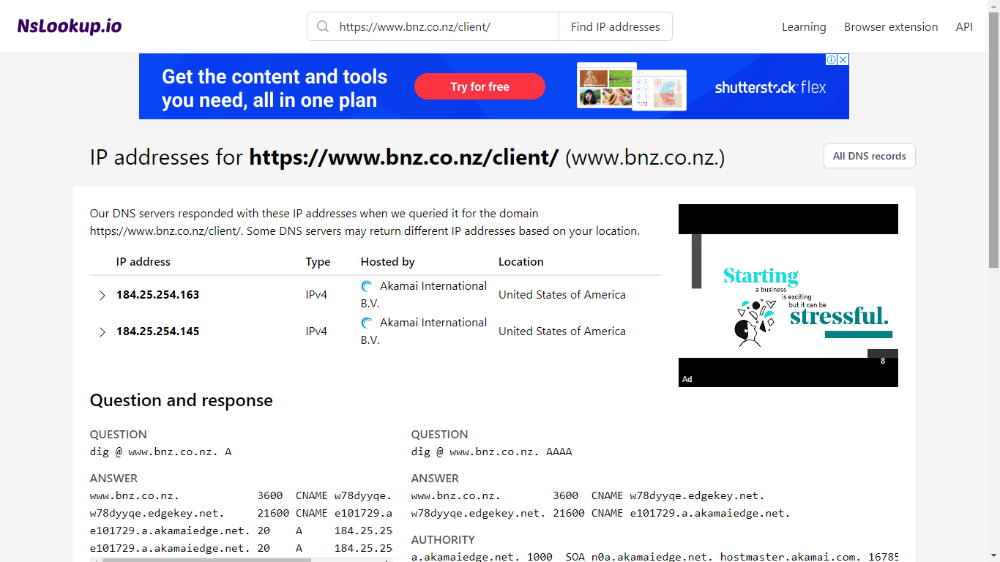
First obtain the banks cloud server IP address.
https://www.nslookup.io/website-to-ip-lookup/
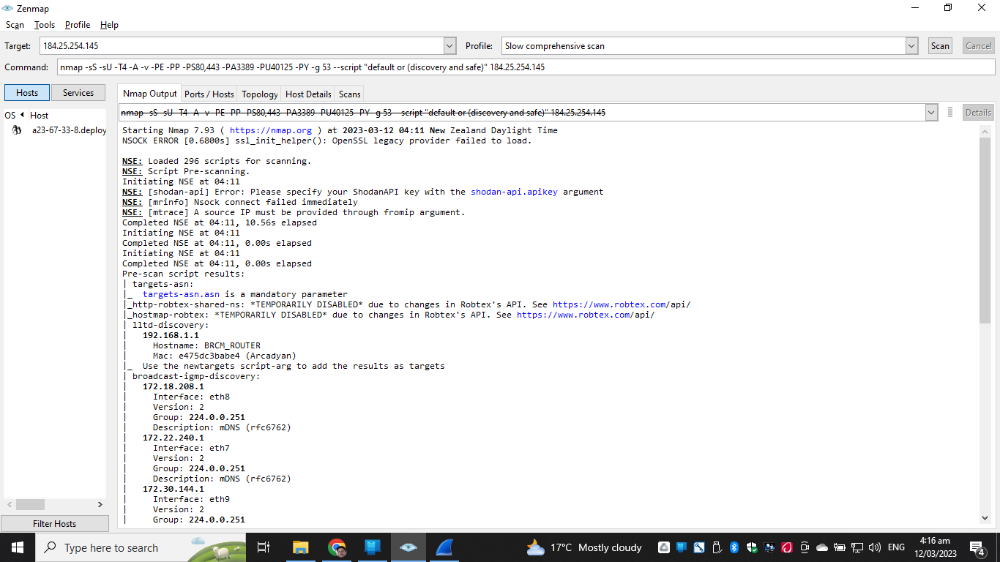
Then use https://nmap.org/zenmap/ Nmap Scanner utility to obtain cloud servers mac address and open ports.
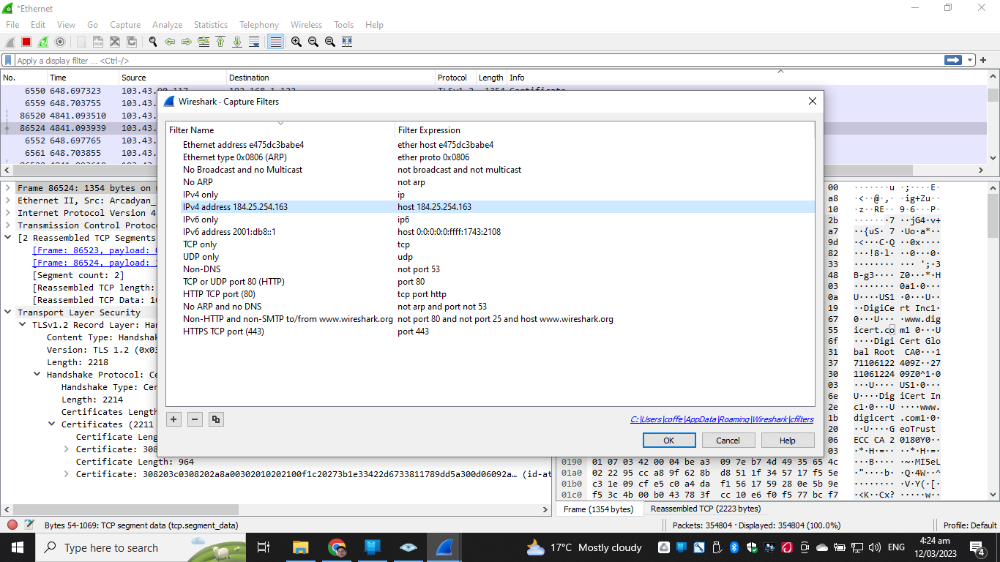
Now use https://www.wireshark.org/ Wireshark to capture the servers certificate and apply filter with MAC address, IP address and ports of packets you want to capture.
Either go to the website or use Nmap scan to obtain the server certificate from cloud provider.
Now look for server certificate in Wireshark and notice the IP address is different as the certification server is probably independent internal server although the MAC address being served is from the cloud providers router.
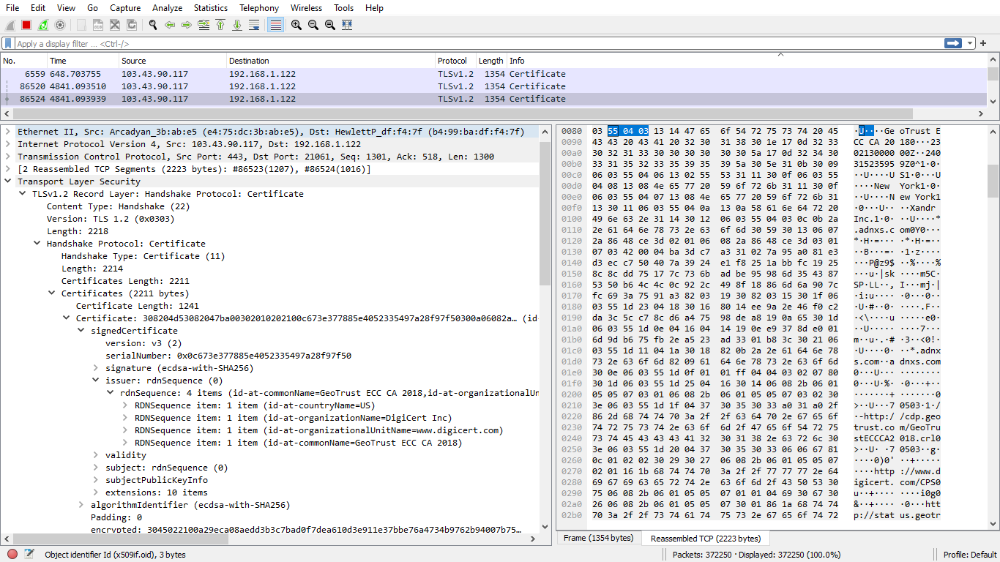
Host the websites domains you have downloaded with https://www.httrack.com/ HTTrack website copier.
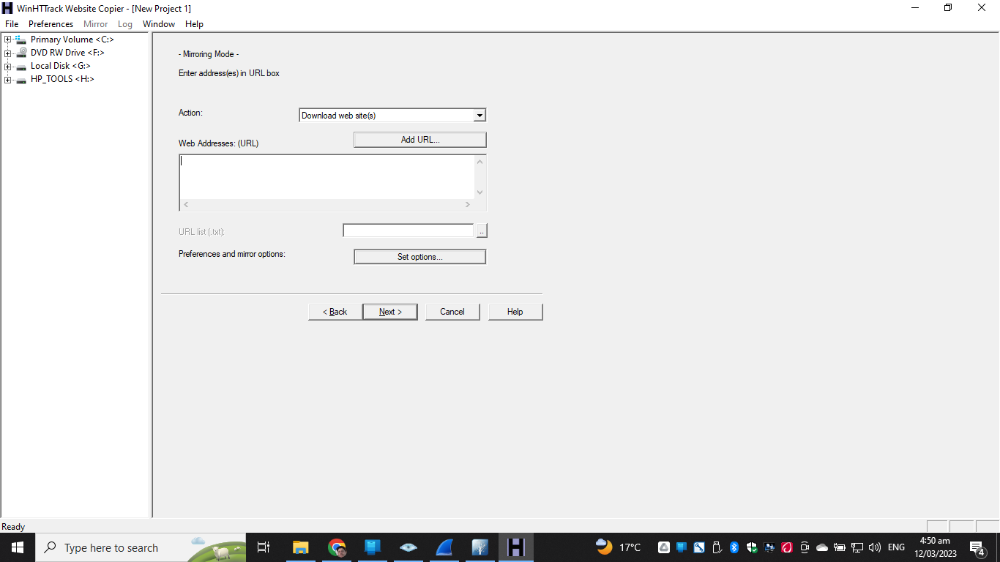
Copy the certificate and save as .pem file for later website spoofing on Apache web server.
Use https://directory.apache.org/studio/ Apache web server to host the spoofed website.
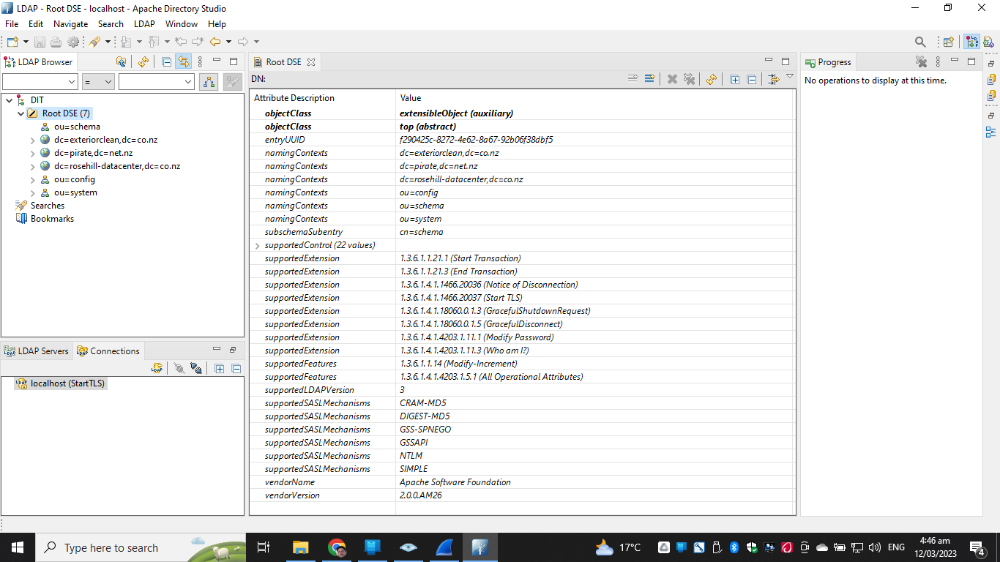
Then host the site and wait for root DNS records to be updated and collect as much bank customer details as you want.
Be sure to use https://technitium.com/tmac/ Technitium MAC Address Changer and VPN connections to mask your identity from authorities.
For legal reasons I have not downloaded a bank website to be spoofed on my web server.

I.T. Development, Alec Bellamy