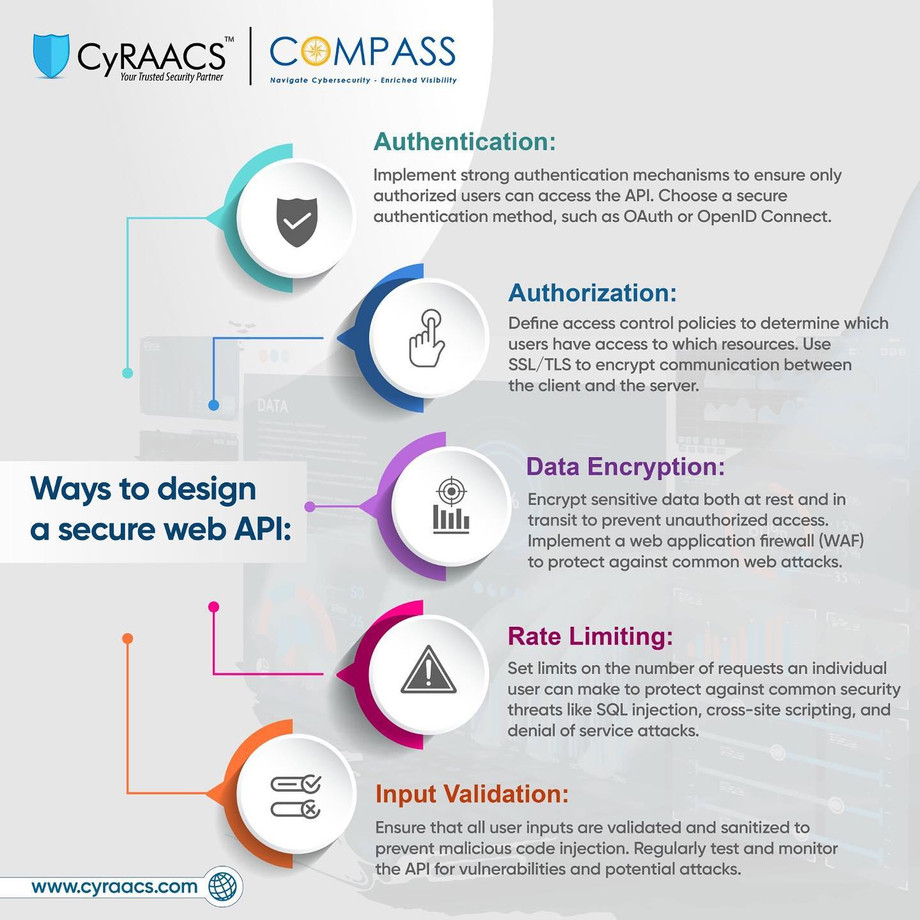
Learn the art of crafting an impenetrable web API as we unveil key strategies. From foolproof authentication protocols to robust encryption techniques, we’ve got you covered.
Discover the power of rate limiting, input validation, and data encryption, to fortify your digital stronghold. Stay ahead of cyber threats and join us on the path to a secure API landscape.
Visit us: https://cyraacs.com/