3. NSO Group and the Pegasus Solution
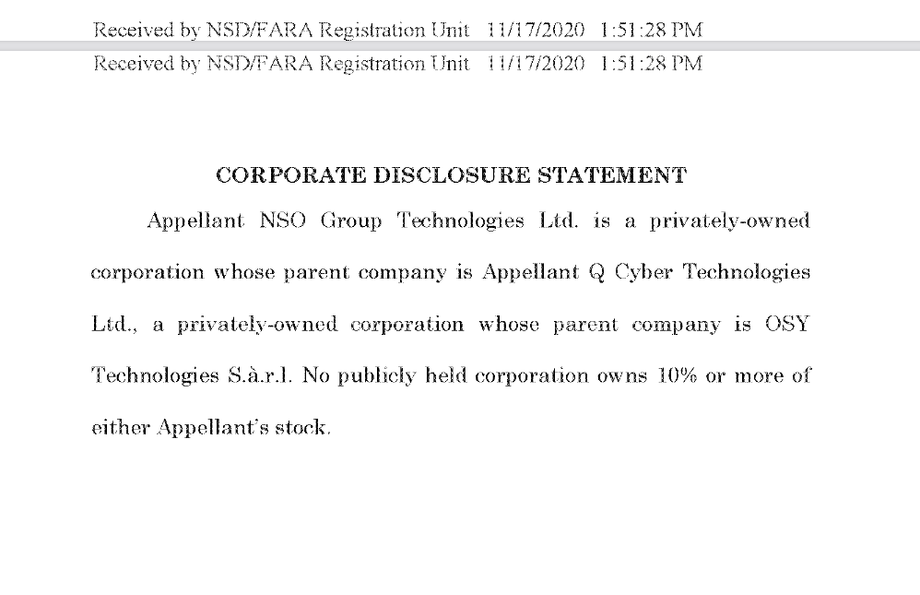
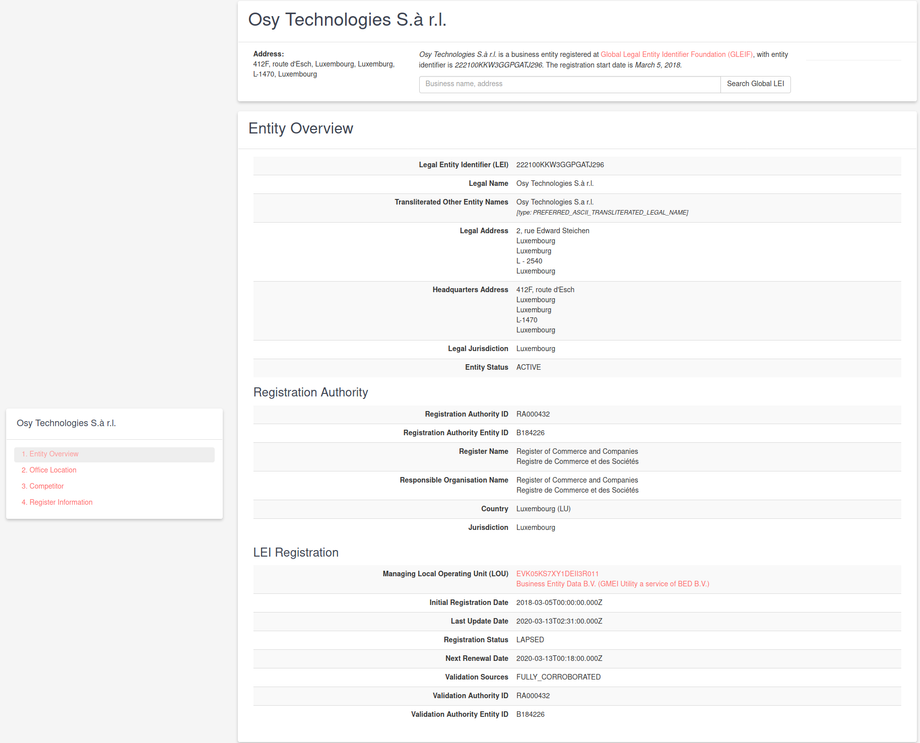
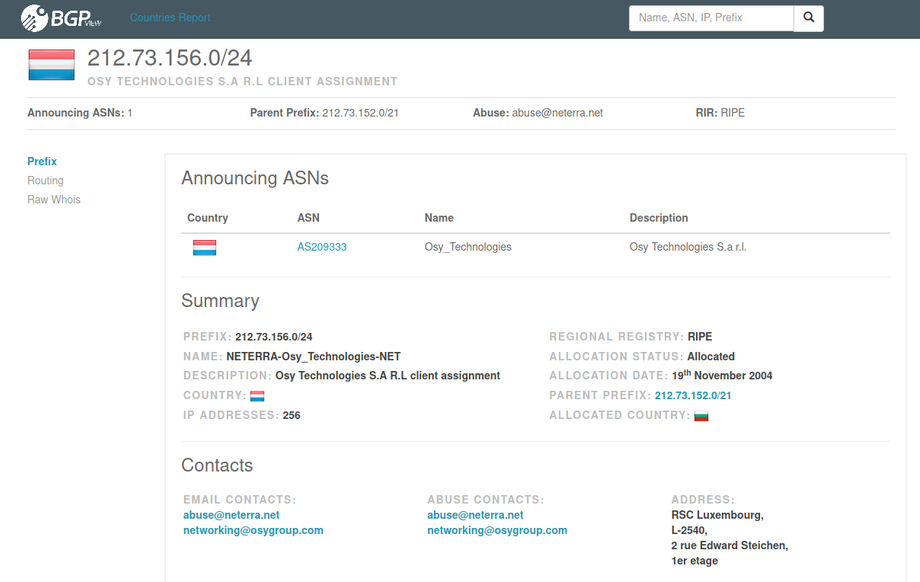
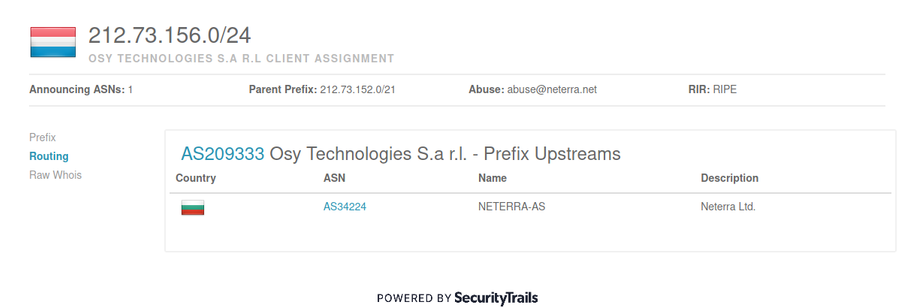
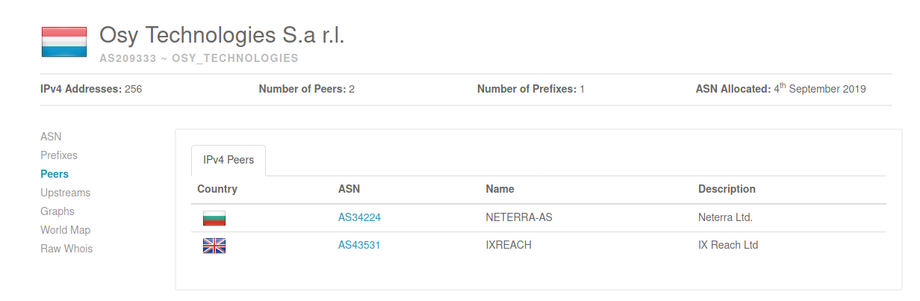
The attack on Mansoor appears to have used Pegasus, a remote monitoring solution sold by NSO Group Technologies Ltd (see Section 6: Linking NSO Group Products to the Attack on Mansoor). NSO Group, based in Herzelia, Israel (CR# 514395409), develops and sells mobile phone surveillance software to governments around the world. The company describes itself as a “leader” in “mobile and cellular Cyber Warfare,” and has been operating for more than six years since its founding in 2010.
NSO Group appears to be owned by a private equity firm with headquarters in San Francisco: Francisco Partners Management LLC, which reportedly acquired it in 2014 after approval from the Israeli Defense Ministry. However, as of November 2015, Francisco Partners was reportedly exploring selling NSO Group, with a stated valuation of up to $1 billion. Interestingly, Francisco Partners previously invested in Blue Coat, a company selling network filtering and monitoring solutions, whose technology has been used by repressive regimes according to previous Citizen Lab research.
NOTE: 2020 OWNERSHIP DETAILS REVEALED in US Disctrict Court
Figure 4: Image from an NSO Group brochure posted on SIBAT (The International Defense Cooperation Directorate of the Israel Ministry of Defense).
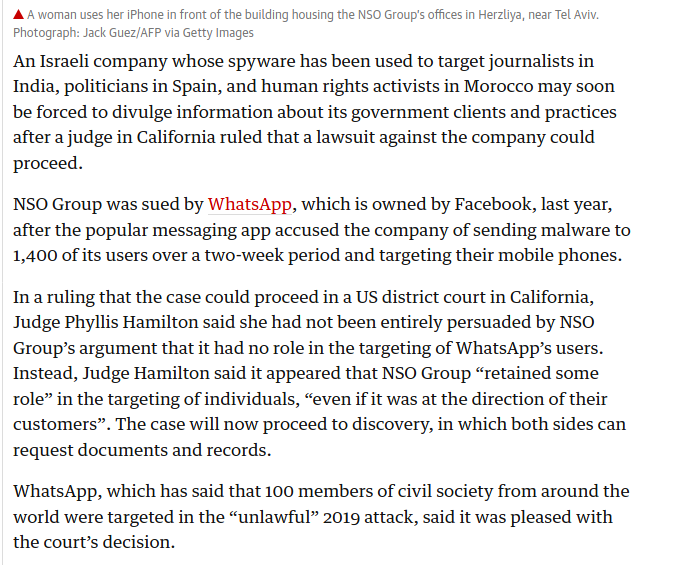
In mid-2020, a mobile phone belonging to an Al Jazeera Arabic investigative team was hacked. Over the next few months, reporter Tamer Almisshal and the Canadian research group Citizen Lab investigated Pegasus, the sophisticated spyware used.
Pegasus is manufactured by an Israeli technology company called the NSO Group and is among the most advanced spyware in the world. It can access and infiltrate a smartphone without the owner clicking a link, opening an email or even answering their phone - meaning it can go undetected.
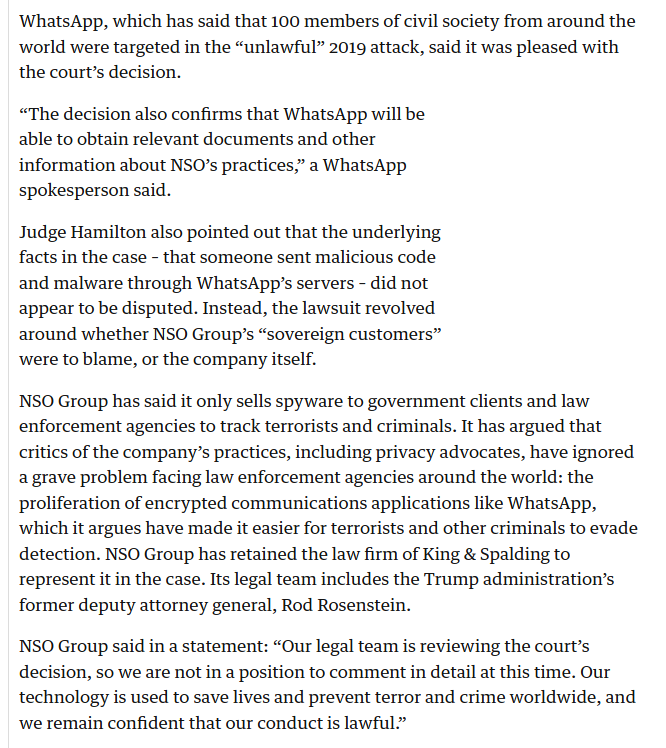
This investigation exposes how Pegasus works, how governments like Saudi Arabia and the UAE have bought the hugely expensive spyware and how it has been used beyond the stated intentions of the NSO Group of “developing technology to prevent and investigate terror and crime” - including to target journalists.
Note: We are not releasing the malicious files at this time to protect the integrity of ongoing investigations.
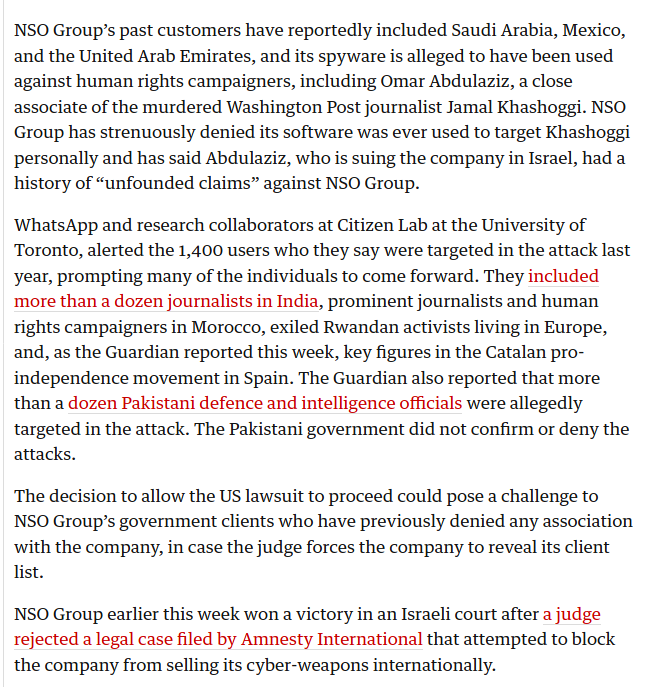
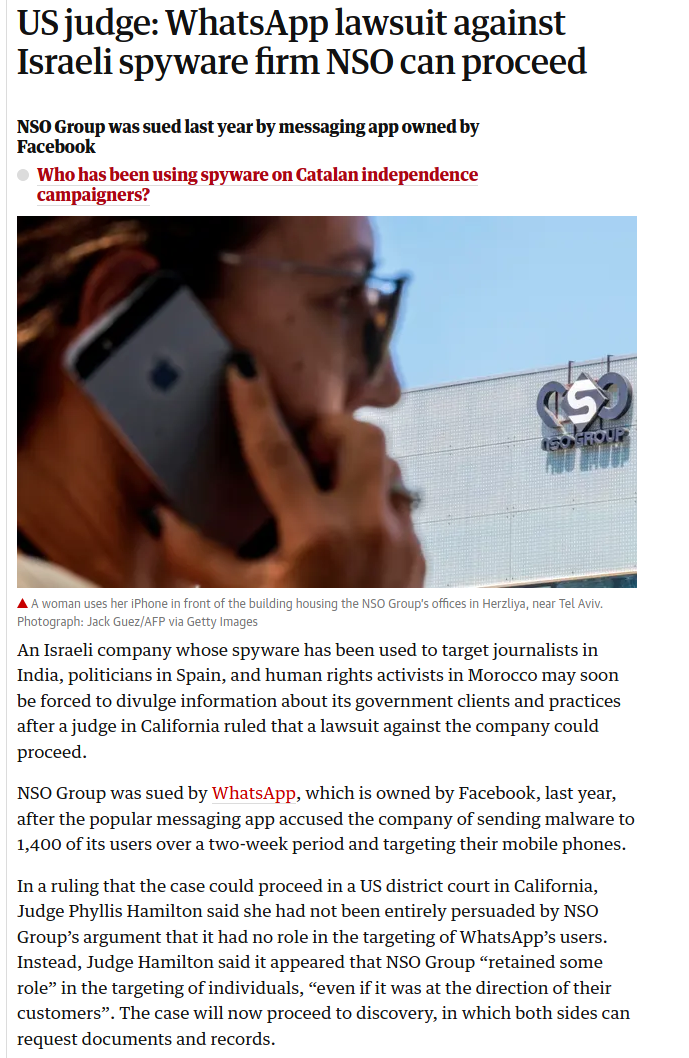
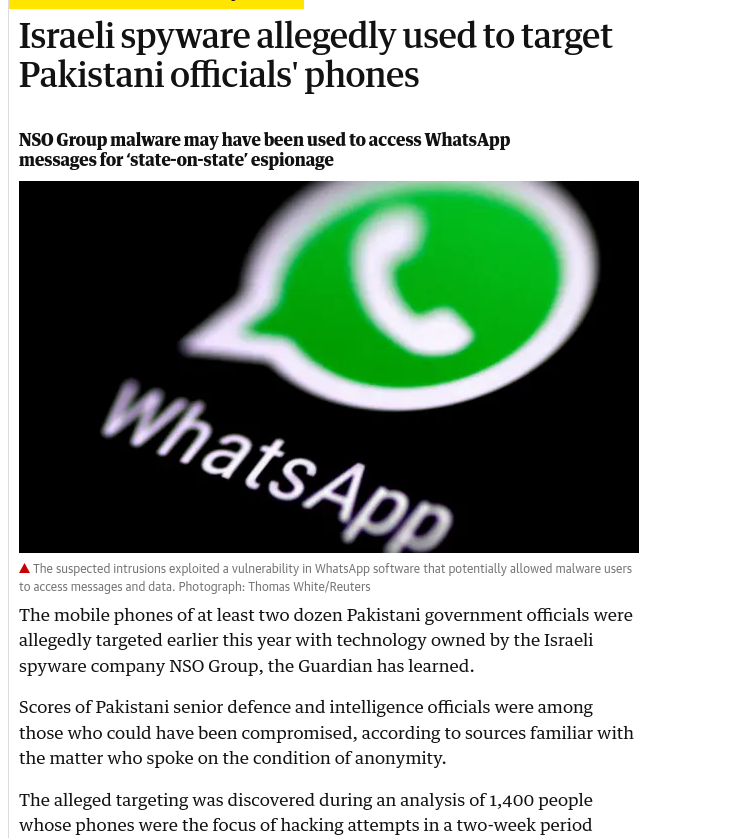
https://www.theguardian.com/world/2020/jan/16/israeli-spyware-firm-nso-hacking-case
https://web.archive.org/save/https://www.nsogroup.com/
https://www.issworldtraining.com/AboutUS.html
https://www.issworldtraining.com/
ABOUT US
Founded in 1980, TeleStrategies is the leading producer of Hi-Tech Investigative Technology training conference events in the United States. Since its launch, the firm has produced over three hundred industry events attracting over 30,000 Law Enforcement and 10,000 telecommunications professionals globally.
ISS World Programs, Intelligence Support Systems the world's largest gathering of Law Enforcement, The Government Intelligence Community, Defense and Homeland Security Analysts, responsible for deploying Electronic Surveillance, Real-Time Video Analytics and Cyber Threat Detection products using (AI) Artificial Intelligence and other Hi-Tech Products. ISS World government attendees are responsible for investigating drug trafficking, cyber money laundering, human trafficking, terrorism and other criminal activities conducted over today's Telecommunications Network, the Internet, DarkNet and Social Media
For year 2019/2020 ISS World has scheduled five global programs:
ISS World North America in Washington, 4-6 September 2019
ISS World Latin America in Panama City, 28-30 October 2019
ISS World Asia in Kuala Lumpur, 3-5 December 2019
ISS World MEA in Dubai, 9-11 March 2020
ISS World Europe in Prague, 9-11 June 2020
In addition to the ISS World Programs, TeleStrategies also provides specialized education seminars and webinars on: DarkWeb, 5G Intercept, TOR Hidden Services, Defeating Encryption and Cybercurrency Transactions Investigation.
Please contact Tatiana Lucas, Director ISS World Programs by email at: talucas@telestrategies.com for more information.
Sincerely,
The TeleStrategies Team
ISS World Training |
TeleStrategies |
Contact Us |
About Us |
TeleStrategies' Privacy Policy
Copyright © 2018 by TeleStrategies, Inc. 6845 Elm Street Suite 310, McLean, VA 22101
voice: 703-734-7050 fax: 703-893-3197 email: info@telestrategies.com
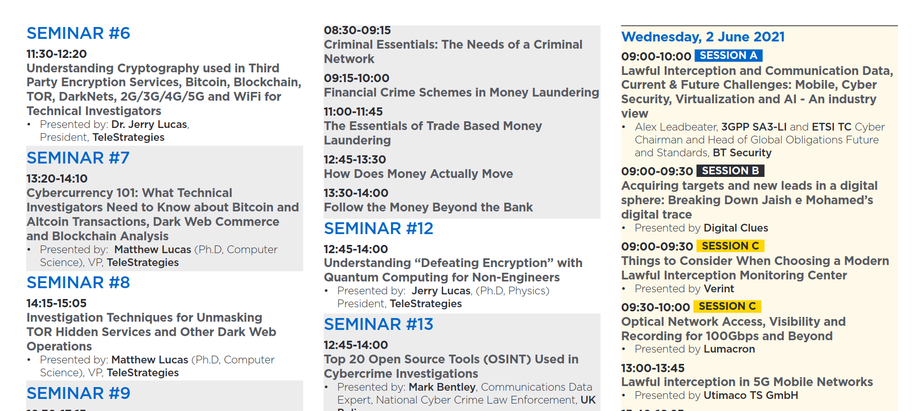
AGENDA : 1 - 3 June 2021
ISS World Europe is the world's largest gathering of Regional Law Enforcement, Intelligence and Homeland Security Analysts, Telecoms as well as Financial Crime Investigators responsible for Cyber Crime Investigation, Electronic Surveillance and Intelligence Gathering.
ISS World Programs present the methodologies and tools for Law Enforcement, Public Safety, Government and Private Sector Intelligence Communities in the fight against drug trafficking, cyber money laundering, human trafficking, terrorism and other criminal activities conducted over today's telecommunications network, the Internet and Social Media.
Track 1: Lawful Interception and Criminal Investigation Training
Track 2: LEA, Defense and Intelligence Analyst Product Demonstrations
Track 3: Social Network Monitoring, Artificial Intelligence and Analytics Product Training
Track 4: Threat Intelligence Gathering and Cyber Security Product Training
Track 5: Investigating DarkWeb, Bitcoin, Altcoin and Blockchain Transaction
Track 6: Mobile Signal Intercept Training and Product Demonstrations
Track 7: Electronic Surveillance Training and Product Demonstrations
Track 8: 5G Lawful Intercept, Tracking and Forensics Product Training
Plus Special Training Seminars lead by Law Enforcement Officers and Ph.D. Scientists
ISS World Europe 2021 Program Agenda
Training Seminars Led by Law Enforcement Officers and Ph.D., Computer Scientists
25 classroom training hours, presented by Law Enforcement Officers and Ph.D. Scientists
Charles Cohen, Vice President at NW3C, the National White Collar Crime Center, Professor in Practice Criminal Justice, Indiana University and Retired Captain, Indiana State Police
(6 classroom hours)
Mark Bentley, Communications Data Expert, National Cyber Crime Law Enforcement, UK Police
(7 classroom hours)
Jerry Lucas (Ph.D., Physics), President, TeleStrategies
(4 classroom hours)
Matthew Lucas (Ph.D., Computer Science), VP, TeleStrategies
(2 classroom hours)
Vladimir Vesely (Ph.D., Computer Science) Researcher, Brno University of Technology
(3 classroom hours)
Tuesday, 1 June 2021
Seminar #1
08:30-15:05
Online Social Media and Internet Investigations
Presented by: Charles Cohen, Cohen Training and Consulting, LLC, also holds the position of Vice President at NW3C, the National White Collar Crime Center, Professor in Practice Criminal Justice, Indiana University and Retired Captain, Indiana State Police
08:30-09:20
The role of Online Social Media OSINT in Predicting and Interdicting Spree Killings: Case Studies and Analysis
09:25-10:15
OSINT and Criminal Investigations
10:35-11:25
Metadata Exploitation in Criminal Investigations
11:30-12:20
EXIF Tags and Geolocation of Devices for Investigations and Operational Security
13:20-14:10
Case Studies in Metadata Vulnerability Exploitation and Facial Recognition
14:15-15:05
What Investigators Need to Know about Emerging Technologies Used to Hide on the Internet
Seminar #2
08:30-15:05
Practitioners Guide to Internet Investigations
Presented by: Mark Bentley, Communications Data Expert, National Cyber Crime Law Enforcement, UK Police
The aim of this 1-day seminar is to take the attendees from the basics of understanding the Internet,
how to find data, through to a full understanding of best practice of an Internet investigator, building their OSINT toolbox, and having awareness and knowledge of all the tools available to achieve this. It is aimed primarily at the investigator, delivered from the perspective of detective, to empower them to have the best methodology and tradecraft to profile and catch suspects.
This is exclusively Law Enforcement only, as Practical examples, covert and investigative methodology and tradecraft will be given throughout the seminar.
08:30-09:20
The Internet, and how suspects leave a Digital Footprint. How the system works for us, as investigators
09:25-10:15
Recognizing Traffic Data and digital profiling via social networks and devices - digital shadows
10:35-11:25
WIFI, geolocation, and Mobile Data traces and tracking
11:30-12:20
Awareness of Emerging Technologies, Masking Tech and Tools, TOR and proxies
13:20-14:10
Advanced Techniques in Tracing Suspects, and lateral problem solving
14:15-15:05
Open Source Tools, resources and techniques - A walk through my free law enforcement open source tools site
Seminar #3
08:30-09:20
Understanding Mobile 2G, 3G, 4G & 5G Infrastructure and Law Intercept for Technical Investigators
Presented by: Dr. Jerry Lucas, President, TeleStrategies
This webinar addresses the infrastructure evolution of 2G to 3G to 4G to 5G and the impact on lawful interception.
Seminar #4
09:25-10:15
Transitioning Lawful Interception Network Core Features from 4G to 5G: What's it Looking Like and Challenges Ahead
Presented by: Matthew Lucas (Ph.D, Computer Science), VP, TeleStrategies
Cellular market analysts collectively have identified 5G services deployed in over 400 cities spread over 30 or so countries. The one common feature of all these operations is that they are providing 5G services with a 4G/5G hybrid network infrastructures or so called non-Stand Alone (NSA) architecture. (Full description below Track 9)
Seminar #5
10:35-11:25
Cybercurrency 101: What Technical Investigators Need to Know about Bitcoin and Altcoin Transactions, Dark Web Commerce and Blockchain Analysis
Presented by: Matthew Lucas (Ph.D, Computer Science), VP, TeleStrategies
This 101-training seminar is an introduction to Bitcoin, how the system is used to support criminal activities (e.g. Dark Web) and why technical investigators need to understand the basic Bitcoin transaction mechanism (Blockchain) to successfully defeat 21st century criminals and terrorist actions. Specifically, this introduction to Bitcoin for technical investigators
Seminar #6
11:30-12:20
Understanding Advanced Techniques to Defeat (or Work Around) Encrypted Third Party Services, Bitcoin Anonymity, TOR/HS and iPhone Encryption
Presented by: Matthew Lucas (Ph.D, Computer Science), VP, TeleStrategies
You can’t defeat today’s encryption (at least not that we know of) but law enforcement and the government intelligence community can “Work around encryption” for a price. Once you identify a target using commercially available encryption products or services (and with enough resources or money) government can defeat the target near 100% of the time.
Seminar #7
16:30-17:15
SSL/TLS Interception Workshop
Presented by: Vladimir Vesely (Ph.D., Computer Science) and Jan Pluskal, Researchers, Brno University of Technology
The presentation introduces methods for intercepting TLS/SSL connections. The focus is on man-in-
middle attack employing TLS/SSL proxy and other ways how to obtain session's private keys. Speakers will outline necessary theory (including the history of SSL/TLS framework design), well-known attacks (including OpenSSL Hearthbleed, Logjam or BEAST) and industry standard tools (such as Wireshark, NetFox Detective, Fiddler Proxy and SSL-Split). The session will also include a live demonstration of MitM attack on HTTPS connections enhanced with form-logging JavaScript injection. Participants will receive free of charge access to test-bed, which consists of real devices (and their traffic) including the prototype of our hardware probe decrypting SSL/TLS on-the-fly.
Thursday, 3 June 2021
Seminar #8
13:00-14:00
Understanding "Defeating Encryption" with Quantum Computing for Non-Engineers
Presented by: Jerry Lucas, (Ph.D, Physics) President, TeleStrategies
This one hour, session is for cyber security executives and specialists who have the responsibility of assessing the lead time they have before deploying quantum safe cryptography solutions but don't have a technical background. If you believe nation state security agencies are developing quantum computing to decrypt your past and future intercepted transmission sessions, this high-level webinar should be a must attend briefing.
And to do this you need to understand how a quantum computing circuit works when designed for the sole purpose of defeating public key encryption.
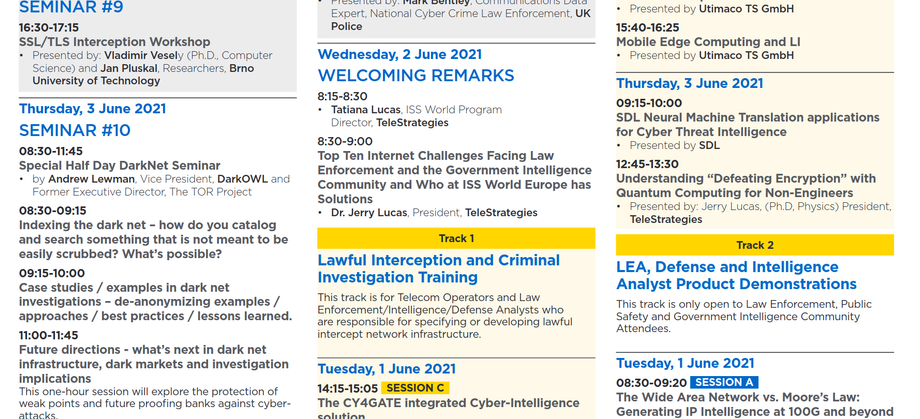
Seminar #9
13:00-14:00
Top 20 Open Source Tools (OSINT) Used in Cybercrime Investigations
Presented by: Mark Bentley, Communications Data Expert, National Cyber Crime Law Enforcement, UK Police
Pre-Conference Sessions Description At The End of Agenda PostinG
Wednesday, 2 June 2021
Welcoming Remarks
| 8:15-8:30 |
Tatiana Lucas, ISS World Program Director, TeleStrategies |
|
8:30-9:00 |
Top Ten Internet Challenges Facing Law Enforcement and the Intelligence Community and Who at ISS World Europe has Solutions |
ISS World Europe Exhibit Hours:
Wednesday, 2 June 2021
10:00-18:15
Thursday, 3 June 2021
10:00 -14:00
Track 1: Lawful Interception and Criminal Investigation Training
This track is for Telecom Operators and Law Enforcement/Intelligence/Defense Analysts who are responsible for specifying or developing lawful intercept network infrastructure.
Tuesday, 1 June 2021
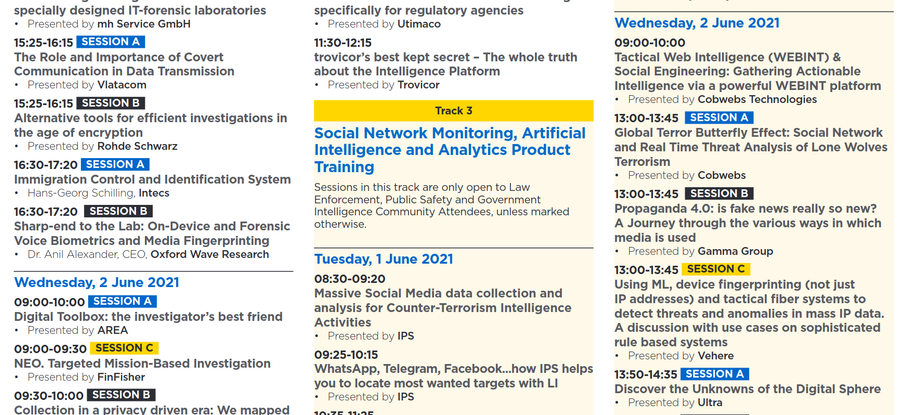
14:15-15:05 Session A
Accelerating investigation workflows with specially designed IT-forensic laboratories
Presented by mh Service GmbH
14:15-15:05 Session B
Memento Labs, the evolution of lawful 360˚ remote surveillance
Presented by Memento Labs
14:15-15:05 Session C
The CY4GATE integrated Cyber-Intelligence solution
Providing Law Enforcement and Intelligence agencies with a “target centric” approach that allows to control and combine together in real-time all the information retrieved by the target under surveillance, levering on multiple class of active and passive sensors.
Presented by CY4GATE
15:25-16:05 Session A
ETSI/3GPP LI/RD Standards Update
Alex Leadbeater, 3GPP SA3-LI and ETSI TC Cyber Chairman and Head of Global Obligations Future and Standards, BT Security
Carmine Rizzo, ETSI TC LI Technical Officer and 3GPP SA3LI Secretary, ETSI
Martin Kissel, ETSI TC LI Chairman and Coordinator Lawful Interception, Telefónica Germany
15:25-16:05 Session B
How Far States have to go to Secure the Net
-What is Regulatory Compliance / Digital Enforcement
-Why do governments need such solutions
-What are countries doing about it (use cases from the public sources)
Joseph Dadon, VP Sales, Allot
16:10-17:00 Session A (Continued from 15:25-16:05)
ETSI/3GPP LI/RD Standards Update
Alex Leadbeater, 3GPP SA3-LI and ETSI TC Cyber Chairman and Head of Global Obligations Future and Standards, BT Security
Carmine Rizzo, ETSI TC LI Technical Officer and 3GPP SA3LI Secretary, ETSI
Martin Kissel, ETSI TC LI Chairman and Coordinator Lawful Interception, Telefónica Germany
16:10-17:00 Session B
Enhancing Lawful Interception with the Five Elements of Cyber Law Enforcement
Criminal and terror organizations are using cyberspace to enhance operations and grow globally. Increased sophistication and the large variation of information channels are stretching intelligence agencies and police resources. Understanding the elements of Cyber Law Enforcement and efficiently utilizing them is key to the effective interception of outlaw activities.
Presented by Toka
Wednesday, 2 June 2021
09:00-10:00 Session A
Lawful Interception and Communication Data, Current & Future Challenges: Mobile, Cyber Security, Virtualization and AI - An industry view
Alex Leadbeater, 3GPP SA3-LI and ETSI TC Cyber Chairman and Head of Global Obligations Future and Standards, BT Security
09:00-9:30 Session B
Protecting Mobile networks and Infrastructure from External Threat Actors
Presented by AdaptiveMobile Security
09:00-09:30 Session C
Things to Consider When Choosing a Modern Lawful Interception Monitoring Center
Presented by Verint
09:30-10:00 Session B
Optical Network Access, Visibility and Recording for 100Gbps and Beyond
Presented by Lumacron
16:30-17:15
SSL/TLS Interception Workshop
Vladimir Vesely (Ph.D., Computer Science) Researcher, Brno University of Technology
Thursday, 3 June 2021
11:45-12:30
Overview of CC-Driver and RAYUELA Projects for Recognizing Human Factors and Drivers of Young Cybercriminality
Rubén Fernández, Àrea de Protecció Ciutadana, Valencia Local Police
13:00-14:00
Understanding "Defeating Encryption" with Quantum Computing for Non-Engineers
Presented by: Jerry Lucas, (Ph.D, Physics) President, TeleStrategies
Track 2: LEA, Defense and Intelligence Analyst Product Demonstrations
This track is only open to Law Enforcement, Public Safety and Government Intelligence Community Attendees.
Tuesday, 1 June 2021
08:30-09:20 Session A
The Wide Area Network vs. Moore's Law: Generating IP Intelligence at 100G and beyond
Gene Litt, CTO, NetQuest
09:25-10:15 Session A
Carrier in Carrier Analysis: Determine the impact of Carrier in Carrier technology on your satellite monitoring capabilities
Presenting the challenges posed by Carrier in Carrier technologies and VASTech’s approach to the analysis of Carrier in Carrier signals and the separation of Symmetrical and Asymmetrical Carrier in Carrier Signals.
Presented by VASTech
09:25-10:15 Session B
TOVEK - creating missing knowledge from disparate information sources
Presented by Tovek
10:35-11:25 Session A
NEW METHODS AND TOOLS DESIGNED FOR LAW ENFORCEMENT AGENCIES FOR ADVANCED CRIMINAL INVESTIGATION
In this presentation, potential new technologies will be presented to help law enforcement agencies in their day-to-day law enforcement tasks. The focus of the session will be on practical use cases and scenarios for prosecution, that also takes future technological developments into account.
Presented by Utimaco
10:35-11:25 Session B
Efficient Cryptanalysis Infrastructure - Doing More with Less
Presented by SciEngines
11:30-12:20 Session A
Different Intelligence Sources combined under a single analytical platform – an innovative approach
Presented by Gamma Group
11:30-12:20 Session B
Product Demonstration Session
Presented by BAE Systems AI
13:20-14:10 Session A
ATIS PANDORA - simplify investigation with one platform
Presented by ATIS
13:20-14:10 Session B
New experience gained from Voice Biometrics and Speech Analytics deployments
Presented by Phonexia
14:15-15:05 Session A
Cyber Intelligence in Our Increasingly Privacy & Security Conscious Environment
Presented by Wintego
14:15-15:05 Session C
Commercial SIGINT - unrestricted, global and large-scale accurate geo-monitoring and profiling of connected devices
VP Sales and Marketing, GeoGence
15:25-16:15 Session A
The Role and Importance of Covert Communication in Data Transmission
Presented by Vlatacom
15:25-16:15 Session B
How to transform network data into intelligence in spite of encrypted and obfuscated IP traffic
Presented by Rohde Schwarz
16:30-17:20
Session Title TBA
Presented by ClearTrail Technologies
Wednesday, 2 June 2021
09:00-10:00 Session A
Setting standards in Cyber Technology & Defense
Presented by NSO Group
09:00-09:30 Session C
NEO. Targeted Mission-Based Investigation
Presented by FinFisher
09:00-10:00 Session D
Industry Secrets of end-to-end data Collection and Analysis: How technology is changing everything and what you need to do, now!
Presented by BAE Systems AI
09:30-10:00 Session B
Collection in a privacy driven era: We mapped out the collection options
Presented by Verint
09:30-10:00 Session C
WiFi Intelligence Gathering - A Key Piece of the Strategic Intelligence Puzzle
Presented by FinFisher
13:00-13:45 Session A
Advanced Tactical Interception and Data Extraction Vectors
Presented by Merlinx
13:00-13:45 Session B
Digital Toolbox: the investigator’s best friend
Presented by AREA
13:00-13:45 Session C
A Safe Landing based approach to Sensitive and Urban Scenario Counter-Drone Defense
Presented by D-Fend
13:45-14:30
Automating forensic Speaker Recognition for Cyber Crime units
Presented by ATIS
15:00-15:45 Session A
LIMS, only black box! Or can it bring additional value to LEAs?
Presented by Sedam
15:00-15:45 Session B
Making the analyst smarter with Intellexa’s Insight
The art of extracting meaningful intelligence from a multitude of sources and vast amounts of data
Presented by Advanced Systems
15:45-16:30
Encrypted or not - every IP-packet tells a story
Mark Uldahl, CTO, XCI A/S
16:30-17:15 Session B
Illuminating the Dark - Technologies for Unmasking Darknet Criminals
Presented by FinFisher
16:30-17:15 Session C
Live Demo. Real Investigation, from OSINT and exfiltration to active cyber security tools (Cyberwarfare).
How to follow the targets in the cyberspace and exfiltrate information, finally using Thor Hammer to neutralize their connected systems.
Presented by MOLLITIAM CYBERINTELLIGENCE
Thursday, 3 June 2021
08:30-09:15 Session A
Guess who is using THAT App in your Country. Metadata as IP Intelligence
Presented by AREA
08:30-09:15 Session B
Fibre Signal Analysis: What intelligence value does a fibre link contain?
Presenting VASTech’s approach to Signal Analysis, Protocol Analysis, Application Classification, Metadata Exploration and Content Evaluation on fibre optic links on a single platform. Enabling agencies to obtain maximum value by understanding the content of a fibre and capturing the useful information.
Presented by VASTech
09:15-10:00 Session A
Taking advantage of technology breakthroughs to advance your investigations
As investigations rely on more digital sources and digital data, investigators become overwhelmed by the volume and complexity, making it even more difficult to pinpoint critical case evidence. Learn how you can leverage Artificial Intelligence and Machine Learning to advance your investigation, find critical insights and accelerate the time to evidence.
Muna Assi, Senior Product Marketing Manager, Cellebrite
09:15-10:00 Session B
Practical and creative example of modifying Android OS by HEX editing system files, and having regular applications to achieve surveillance.
Denis Cuculic, CEO ex. Head of Technical Department, PRO4SEC
11:00-11:45 Session A
trovicor’s best kept secret – The whole truth about the Intelligence Platform
Presented by Trovicor
11:00-11:45 Session B
Following the black rabbit - Advanced targets monitoring
Presented by Memento Labs
11:45-12:30
Data Enrichment Techniques and Sources for Internet Investigations
Presented by Packet Forensics
Track 3: Social Network Monitoring, Artificial Intelligence and Analytics Product Training
Sessions in this track are only open to Law Enforcement, Public Safety and Government Intelligence Community Attendees, unless marked otherwise.
Tuesday, 1 June 2021
08:30-09:20 Session A
Massive Social Media data collection and analysis for Counter-Terrorism Intelligence Activities
Presented by IPS
09:25-10:15
WhatsApp, Telegram, Facebook...how IPS helps you to locate most wanted targets with LI
Presented by IPS
11:30-12:20
Using AI-based Risk Scoring for Multi-source Target Acquisition and Prioritization
Presented by Simulation Software & Technology, S2T
13:20-14:10 Session A
Combating Threats with Advanced AI-Driven Technologies – Leveraging open source data to anticipate and prevent future attacks
Presented by Voyager Labs
13:20-14:10 Session B
SCOPE Product – A Real Life Scenario (demo)
Presented by Innosystec
14:15-14:40 Session A
Combating Threats with Advanced AI-Driven Technologies – Leveraging open source data to anticipate and prevent future attacks
Presented by Voyager Labs
14:15-14:40 Session B
Automatic Exploitation of Social Network, Deep and Dark Web to complement traditional Lawful Interception Infrastructure for Target Profiling.
Presented by IPS
14:40-15:05 Session B
Machine Learning in a Command and Control Centre for covert field operations and situation awareness
Presented by IPS
15:25-16:15 Session A
How social media platforms are limiting the API approach and advanced DB queries
Presented by Verint
15:25-16:15 Session B
Multimedia Monitoring and Forensics Laboratory
Presented by Everis
16:30-17:20 Session A
The hype of AI usage in intelligence is facing multiple challenges
Presented by Verint
16:30-17:20 Session C
Uncovering Intelligence on Messaging Apps
How to track and profile cyber criminals using large sources of data collected on mobile messaging apps
Liran Sorani, Cyber Business Unit Manager, Webhose.io
Wednesday, 2 June 2021
09:00-10:00
Tactical Web Intelligence (WEBINT) & Social Engineering: Gathering Actionable Intelligence via a powerful WEBINT platform
Presented by Cobwebs Technologies
13:00-13:45 Session A
Global Terror Butterfly Effect: Social Network and Real Time Threat Analysis of Lone Wolves Terrorism
Presented by Cobwebs
13:00-13:45 Session B
Propaganda 4.0: is fake news really so new? A Journey through the various ways in which media is used
Presented by Gamma Group
13:00-13:45 Session C
Using ML, device fingerprinting (not just IP addresses) and tactical fiber systems to detect threats and anomalies in mass IP data. A discussion with use cases on sophisticated rule based systems.
Presented by Vehere
13:00-13:45 Session C
SCOPE Product – Prevent and Predict
Presented by Innosystec
13:45-14:30 Session A
Discover the Unknowns of the Digital Sphere
Presented by Ultra
13:45-14:30 Session B
Follow the digital traces in social media- approaches and best practices to leverage the potential of cloud data in your investigations
As more people spend time on social applications, investigations today require data that resides beyond the mobile device. We will explore technologies that can help you effectively surface evidence from public and private domain data, in cloud-based applications, services and web pages to identify suspects and solve cases fast.
Muna Assi, Senior Product Marketing Manager, Cellebrite
15:00-15:45 Session A
Unlocking the full potential of speech technologies to transform OSINT and COMINT
Presented by Vocapia
15:00-15:45 Session B
trovicor’s best kept secret – The whole truth about the Intelligence Platform
Presented by Trovicor
15:00-15:45 Session C
Transforming Investigations & Risk Assessment with Artificial Intelligence
Presented by Voyager Labs
15:45-16:20
Session Title TBA
Presented by ClearTrail Technologies
16:30-17:15
Gens.AI, the Cyber Humint solution that can automate the management of virtual identities
Starting from the digital profile creation and its background maintenance, to the execution of under-cover operations on the Internet.
Presented by CY4GATE
Thursday, 3 June 2021
08:30-09:15 Session A
Transforming Investigations & Risk Assessment with Artificial Intelligence
Presented by Voyager Labs
08:30-9:15 Session B
ATIS PANDORA - fast visualization, analysis and fusion of large data sets from different sources
Presented by ATIS
09:15-10:00 Session A
SCOPE Product – Bringing Data to Life
Presented by Innosystec
09:15-10:00 Session B
How to Protect the Status of Data Traffic Without Changing the Status Quo
-DPI as a starting point (watch the network)
-Application Control and Network Management
-Network Security and Traffic Prioritization
Joseph Dadon, VP Sales, Allot
09:15-10:00 Session C
Social Links for Social Media and Open Source intelligence and investigations
Presented by Social Links
11:00-11:45 Session A
Using ML, device fingerprinting (not just IP addresses) and tactical fiber systems to detect threats and anomalies in mass IP data. A discussion with use cases on sophisticated rule based systems.
Presented by Vehere
11:00-11:45 Session B
AI-based Language Technology Solutions to Handle Multi-language OSINT & COMINT
Presented by SYSTRAN
13:00-14:00
Top 20 Open Source Tools (OSINT) Used in Cybercrime Investigations
Mark Bentley, Communications Data Expert, National Cyber Crime Law Enforcement, UK Police
Track 4: Threat Intelligence Gathering and Cyber Security Product Training
This track is only open to Law Enforcement, Public Safety and Government Intelligence Community Attendees
Tuesday, 1 June 2021
9:25-10:15
Live Demo. Real Cyberoperation, invisible control of Android smartphones, Windows/macOS systems and Clouds (hijacking).
Live Demo of the latest technology used to take invisible control of target systems, and lessons learned in tactical operations in the Cyberspace.
Presented by MOLLITIAM CYBERINTELLIGENCE
10:35-11:25
The Matrix Concept – Combining forward-thinking intelligence tools and proven workflows to assemble a coherent intelligence picture (LIVE DEMO)
Presented by Rayzone Group
13:20-14;10
Disrupt cyber threats by unmasking your adversaries
Presented by 4iQ
Wednesday, 2 June 2021
13:00-13:45
Hushmeeting: creating an iron-clad and quantum-safe communication environment
Presented by Feedback Italia
13:45-14:30
Global Signalling Threat Analysis and Insights for Cyber Intelligence
Presented by AdaptiveMobile Security
15:00-15:45
Router based interception – redefining remote monitoring by infiltrating targeted LAN networks (LIVE DEMO)
Presented by Rayzone Group
15:45-16:30
Encrypted & Evasive Traffic: New Visibility with Next-Generation DPI
As cyber attacks become increasingly sophisticated, the effectiveness of detection and investigation capabilities depends more and more on the quality, detail and accuracy of the network traffic information delivered for threat analytics. Discover a new generation of DPI sensors, enriched with flow analytics and advanced data mining techniques, capable of delivering critical visibility into encrypted traffic to support triage for decryption, advanced analytics, anomaly detection and forensics. The sensors can also detect and extract data about traffic using evasive techniques, such as VPNs, anonymizers, covert communications channels, complex tunneling, domain fronting, traffic/file spoofing, etc., and provide data that can be leveraged to identify users and locate devices.
Sebastien Synold, Product Manager, Qosmos DPI Business Unit, ENEA
Thursday, 3 June 2021
08:30-09:15
Worldwide Virtual SIGINT – monitoring digital footprint in order to anticipate and prevent evolving threats (LIVE DEMO)
Presented by Rayzone Group
Track 5: Investigating DarkWeb, Bitcoin, Altcoin and Blockchain Transaction
This track is for law enforcement and private enterprise investigators who have to monitor and investigate the DarkNet along with Bitcoin transactions associated with criminal activities
Note: Some sessions are only open to LEA and Government. These sessions are marked accordingly.
Tuesday, 1 June 2021
10:35-11:25
Cybercurrency 101: What Technical Investigators Need to Know about Bitcoin and Altcoin Transactions, Dark Web Commerce and Blockchain Analysis
Matthew Lucas (Ph.D, Computer Science), VP, TeleStrategies
13:20-14:10
Automated data collection and normalization from clearnet, darknet and deep web sources
Presented by Kofax
14:15-15:05
Live Demonstration of DarkOwl Vision: Darknet Intelligence Discovery and Collection
David Alley, CEO, DarkOWL FZE
(THIS SESSION IS ONLY OPEN TO LEA AND GOVERNMENT ATTENDEES)
15:25-16:15
Offline Darknet web-crawling with the Web-I-Qube
Presented by mh-Service GmbH
(THIS SESSION IS ONLY OPEN TO LEA AND GOVERNMENT ATTENDEES)
16:30-17:20
Identifying Darknet Suspects: When Law Enforcement Hacks
Presented by Searchlight
Wednesday, 2 June 2021
15:45-16:30
Profile, target and investigate the Darknet. Reinventing traditional HUMINT in the Digital Era
Presented by AREA
(THIS SESSION IS ONLY OPEN TO LEA AND GOVERNMENT ATTENDEES)
Thursday, 3 June 2021
08:30-09:15 Session B
Hunting Down Cryptocurrency Users
Vladimir Vesely (Ph.D., Computer Science) Researcher, Brno University of Technology
11:00-11:45 Session B
Understanding Terrorist Fundraising and Drug Money Laundering Using Decentralized Funance (DeFi): P2P Cryptocurrency Transactio with no KYC Request
Karhrman Ziegenbein, Managing Partner, Tomoco Discovery
11:45-12:30 Session B
Understanding Terrorist Fundraising and Drug Money Laundering using, Non-Fungible Tokens (NFT) Blockchain
Karhrman Ziegenbein, Managing Partner, Tomoco Discovery
13:00-14:00
Follow the Cryptocurrency trail to trace the next terrorist
Presented by Verint
Track 6: Mobile Signal Intercept Product Training and Demonstrations
This track is for Law Enforcement, Interior Security and the Government Intelligence Community who must work with cellular and mobile satellite operators regarding mobile location, electronic surveillance and RF intercept.
This track is only open to Law Enforcement, Public Safety and Government Intelligence Community Attendees.
Tuesday, 1 June 2021
8:30-9:20 Session A
SCPC/VSAT Interception in CiC/CuC Scenarios
Presented by Rohde Schwarz
8:30-9:20 Session B
Understanding Mobile 2G, 3G, 4G and 5G Infrastructure, Intercept and Cryptography
Dr. Jerry Lucas, President, TeleStrategies
10:35-11:25
VSAT Networks: Tactical and Strategic Threat Detection and Geolocation
Presented by Kratos
11:30-12:20
Latest techniques of detecting and neutralizing IMSI Catchers and Wi-Fi monitoring systems
Presented by NeoSoft
13:30-14:10
Real-time identification and geo-location in mobile networks: how to identify and get, in real-time, the accurate position of a handset in a mobile network
Presented by Evistel
15:25-16:15 Session B
Hiding from SIGINT - mobile network approach
Presented by MACRO-SYSTEM
16:20-17:20
Distributed IMSI Catching & Private networks
Nick Johnson, CTO & Head of PLM, IP Access
Wednesday, 2 June 2021
09:00-10:00
Empowering field intelligence teams – how Intellexa combines native 3G/4G interception and long range WiFi interception to make field cyber operations more successful than ever
Presented by Intellexa
13:45-14:30 Session A
Strategic intelligence to follow trends and reveal hidden targets
Presented by Advanced Systems
13:45-14:30 Session B
Breaking the borders of tactical cyber-intelligence
Presented by Jenovice
15:00-15:45
Next-generation IMSI Catcher with public number detection: overview of latest developments and trends
Presented by NeoSoft
15:45-16:30
Providence Training Academy
Presented by Providence
Thursday, 3 June 2021
08:30-09:00
Mobile Radio Analysis Solutions with 5G for Government
Presented by Rohde Schwarz
11:45-12:30
Seeing Beyond - Groundbreaking Intelligence Gathering Platform for the IoT Landscape
The IoT landscape is the fastest-growing part of the digital landscape. Groundbreaking intelligence software presents a breakthrough in intelligence gathering, to enhance investigations, operations, and emergency situations, all of which are extremely necessary for the post-COVID-19 era. The presentation will be followed by a product demo.
Presented by Toka
Track 7: Electronic Surveillance Training and Product Demonstrations
This track is for law enforcement investigators and the government intelligence community who are responsible for deploying video, audio and GPS surveillance products and only open to Law Enforcement, Public Safety and Government Intelligence Community Attendees.
Tuesday, 1 June 2021
8:30-9:20
Intelligent Connections - Gathering Intelligence from IoT Made Simple
Presented by Interionet
9:25-10:15
Taking Control with Drone Takeover C-UAS technology for sensitive and urban environments
Presented by D-Fend
11:30-12:20
A new paradigm for covert audio surveillance in large areas
Presented by Commesh
15:25-16:15
Waveguard’s border monitoring and control solutions
Presented by WaveGuard
Wednesday, 2 June 2021
13:00-13:45
Simultaneous use of many Squarehead Audio recorders in complex and challenging acoustic environments.
Stig Nyvold, CEO, Squarehead Technology
15:45-16:20
Seeing Beyond - Groundbreaking Intelligence Gathering Platform for the IoT Landscape
The IoT landscape is the fastest-growing part of the digital landscape. Groundbreaking intelligence software presents a breakthrough in intelligence gathering, to enhance investigations, operations, and emergency situations, all of which are extremely necessary for the post-COVID-19 era. The presentation will be followed by a product demo.
Presented by Toka
16:30-17:15
Border Security and Force Protection Analytics using Passive RF
Presented by Packet Forensics
Track 8: 5G Lawful Interception Product Training
This track is open to all conference attendees.
Tuesday, 1 June 2021
9:25-10:15
Understanding 5G Network Core (NFV, SDN, EDGE Computing and Network Slicing) for Law Enforcement Investigators
Matthew Lucas (Ph.D, Computer Science), VP, TeleStrategies
14:15-15:05
SIGINT in 5G - How to catch an IMSI
Sander de Jong, Group 2000
15:25-16:15
The challenges 5G brings to cellular Security & Surveillance
Nick Johnson, CTO & Head of PLM, IP Access
16:30-17:20
Changing Needs for LEAs with 5G, Location and Encryption
Presented by SS8
Wednesday, 2 June 2021
13:00-13:45
LAWFUL INTERCEPTION IN 5G MOBILE NETWORKS
This session will elaborate the needs and the challenges of lawful interception in current and future wireless networks. Network operators and law enforcement agencies will get practical advice and hear about best practice techniques for the implementation of LI in 5G networks.
Presented by Utimaco
13:45-14:30
Challenges to consider when preparing for the 5G Lawful Interception Era
Presented by Verint
15:00-15:45
LAWFUL INTERCEPTION OF ROAMING TARGETS (S8HR)
S8HR is recognized as the easiest LTE Roaming architecture to implement by many mobile operators. With all mobile traffic traversing the home network, there are lawful intercept limitations when monito- ring VoLTE calls of visiting roamers. In this session we will present solutions to meet these challenges.
Presented by Utimaco
15:45-16:30
Real World Interpretation of 5G LI Requirements and Implicatios for Carriers and LEAs with 5G
Presented by SS8
Training Seminars Led by Law Enforcment Officers and Ph.D Computer Scientists
Tuesday, 1 June 2021
Seminar #1
08:30-15:05
Online Social Media and Internet Investigations
Presented by:Charles Cohen, Vice President at NW3C, the National White Collar Crime Center, Professor in Practice Criminal Justice, Indiana University and Retired Captain, Indiana State Police
08:30-09:20
The role of Online Social Media OSINT in Predicting and Interdicting Spree Killings: Case Studies and Analysis
09:25-10:15
OSINT and Criminal Investigations
10:35-11:25
Metadata Exploitation in Criminal Investigations
11:30-12:20
EXIF Tags and Geolocation of Devices for Investigations and Operational Security
13:20-14:10
Case Studies in Metadata Vulnerability Exploitation and Facial Recognition
14:15-15:05
What Investigators Need to Know about Emerging Technologies Used to Hide on the Internet
Seminar #2
08:30-15:05
Practitioners Guide to Internet Investigations
Presented by: Mark Bentley, Communications Data Expert, National Cyber Crime Law Enforcement, UK Police
The aim of this 1-day seminar is to take the attendees from the basics of understanding the Internet,
how to find data, through to a full understanding of best practice of an Internet investigator, building their OSINT toolbox, and having awareness and knowledge of all the tools available to achieve this. It is aimed primarily at the investigator, delivered from the perspective of detective, to empower them to have the best methodology and tradecraft to profile and catch suspects.
This is exclusively Law Enforcement only, as Practical examples, covert and investigative methodology and tradecraft will be given throughout the seminar.
08:30-09:20
The Internet, and how suspects leave a Digital Footprint. How the system works for us, as investigators
How it works. Why it works. How it works for us .How data traffic leaves a trace ; What the internet is; what is an IP and how is it significant to trace a person. IPv4 and IPv6 – understanding the changes- the benefits and pitfalls for the investigator. The internet has millions of copies of data on it - why, and where can we find this. Tracking and evaluating data. MAC adders tracking.
09:25-10:15
Recognizing Traffic Data and digital profiling via social networks and devices - digital shadows
What data is available. How to harvest and analyze it. Best practice to identify suspects and build profiles. Good practice, virtual data 'housekeeping' and tradecraft .Data collection and interrogation, significance and value. IP usage, exploitation and dynamics; IP plotting and analysis how to look for suspect mistakes and exploit them ( where they show their id). Dynamic approaches to identifying suspects through internet profiles. What investigators get from tech and service providers, and how to analyze it. Investigator capabilities and opportunities.
10:35-11:25
WIFI, geolocation, and Mobile Data traces and tracking
A detectives look at Wi-Fi, attribution, cell site data, GPRS location services and technology. How an investigator can track devices, attribute suspects locations, devices and movement. Unique communication identifiers. Dynamic live time tracing. Geo location services and uses. Online Surveillance and tracking movement and speed.
11:30-12:20
Awareness of Emerging Technologies, Masking Tech and Tools, TOR and proxies
How suspects are using emerging and new technologies.
An introduction to where technology is going, and how Law enforcement can use this to our advantages. dynamic and pro-active problem solving. Darknet, (Deep web) , TOR and IRC use. VOIP, Skype and FaceTime exploits. Advanced data sniffing and profile building. TOR systems, applications and ways to coax offenders out of the system.
13:20-14:10
Advanced Techniques in Tracing Suspects, and lateral problem solving
Using innovative and dynamic methods to trace offenders. Tricks used by suspects and how to combat them- Play them at their own game?. Covert internet investigations. Proxy servers and hiding. Managing collateral intrusion. Reverse and social engineering. Thinking outside the box. Lateral thinking. Possible missed opportunities. Profile building and manhunts through device footprints, speed and movement.
14:15-15:05
Open Source Tools, resources and techniques - A walk through my free law enforcement open source tools site
"Just google it" doesn't work anymore. A look at good tradecraft, practice and methodology in profiling, tracking and tracing digital footprints and shadows on the internet, by means of best available tools. A look at a selection of 200+ tools available on Mark's open source law enforcement tools website, that search engines can’t see, with login and password provided during the session. Do's and do nots. Best tools for best results. When was the last time you 'googled' something in an investigation, and it returned 5 results, all specifically relating to your suspect? This session will teach you how.
Seminar #3
08:30-09:20
Understanding Mobile 2G, 3G, 4G & 5G Infrastructure and Law Intercept for Technical Investigators
Presented by: Dr. Jerry Lucas, President, TeleStrategies
This webinar addresses the infrastructure evolution of 2G to 3G to 4G to 5G and the impact on lawful interception. Specifically;
Network Architecture Evolution from 2G to 3G, 3G to 4G, 4G to 5G regarding radio technology (TDMA, CDMA, OFDM and MIMO), network core from CSFB to VoLTE and SS7 to Diameter.
Encryption, Target Identification and Location: SIM and eSIM cards, IMSI and Target ID, encryption algorithms (A3, A5, A8 and Ki) and basically how user authentication and traffic encryption is accomplished.
Target Location Tracking with CDR analysis, MAC address farming, MITM attacks, SS7 access, IMSI catchers and IT intrusion.
4G to 5G Transition Specifics Understanding 5G Non Stand Alone (NSA) vs. SA 5G, the IMSI catcher issue (myth vs. realities), 5G Cryptography (ECC, SUPI, SUCI), 5G target location enhancement and LTE/NR Internetworking and Co-existance.
5G Spectrum What can 5G deliver with mid vs. high frequency spectrum and what new spectrum bands are soon to be auctioned off
SA 5G Infrastructure Features: NFV, SDN, Edge/Cloud Computing and Network Slicing
Seminar #4
09:25-10:15
Transitioning Lawful Interception Network Core Features from 4G to 5G: What's it Looking Like and Challenges Ahead
Presented by: Matthew Lucas (Ph.D, Computer Science), VP, TeleStrategies
Cellular market analysts collectively have identified 5G services deployed in over 400 cities spread over 30 or so countries. The one common feature of all these operations is that they are providing 5G services with a 4G/5G hybrid network infrastructures or so called non-Stand Alone (NSA) architecture.
In reality lawful interception of non-standalone is not any different from 4G interception regarding new LI feature additions. The next LI challenge will be for 5G SA. This webinar addresses the technical challenges facing law enforcement, 5G operators and ISS vendors. Specifically the four transitions are:
- 5G Network Challenges Identifiers: How are law enforcement going to grab 1gbps traffic streams; backhaul to monitoring centers and filter non-important traffic of interest.
- 5G Edge Cloud Computing: How do you intercept on a 5G operators IT systems, deal with proprietary system protocols, e2e encryption and localized content
- 5G Virtual Network Core: How complicated will this be regarding LI, VoIP on virtual devices and what LI barriers has the IETF created
- 5G Network Slicing: Is this 5G feature restricted to private enterprises or will 5G MVNO’s provide public mobile wireless services, How will law enforcement interconnect with 5G OSS provisioning systems and what is the LI point of interconnection?
Seminar #5
10:35-11:25
Cybercurrency 101: What Technical Investigators Need to Know about Bitcoin and Altcoin Transactions, Dark Web Commerce and Blockchain Analysis
Presented by: Matthew Lucas (Ph.D, Computer Science), VP, TeleStrategies
This 101 training seminar is an introduction to Bitcoin, how the system is used to support criminal activities (e.g. Dark Web) and why technical investigators need to understand the basic Bitcoin transaction mechanism (Blockchain) to successfully defeat 21st century criminals and terrorist actions. Specifically, this introduction to Bitcoin for technical investigators addresses:
- Bitcoin Basics for Technical Investigators
- Understanding Bitcoin Infrastructure, Blockchain and Bitcoin Mining
- How Criminals and Terrorists Use TOR and Dark Web
- Bitcoin Cryptography Demystified (For Non-Math Majors)
- Popular Altcoins used by Criminals and the New Challenges Facing Law Enforcement
Seminar #6
11:30-12:20
Understanding Advanced Techniques to Defeat (or Work Around) Encrypted Third Party Services, Bitcoin Anonymity, TOR/HS and iPhone Encryption
Presented by: Matthew Lucas (Ph.D, Computer Science), VP, TeleStrategies
You can’t defeat today’s encryption (at least not that we know of) but law enforcement and the government intelligence community can “Work around encryption” for a price. Once you identify a target using commercially available encryption products or services (and with enough resources or money) government can defeat the target near 100% of the time.
This session:
- Analyses the top third party encrypted serves (Telegram, Silent Circle, WhatsApp, Skype, Viber,TOR, TOR/HS); the cryptography deployed; why criminals and terrorists choose one over the other; and related LI challenges.
- Presents the common techniques for defeating the encryption deployed in these services, and their success/weakness, including:
- Man in the Middle Attacks
- IT Intrusion (Installing Malware)
- Exploiting bugs in SSL/TLS
- Connecting the “metadata” dots between known targets and communication patterns
- Case studies working around third party encryption case studies, e.g. how was it done!
- TOR / DarkNets (TOR/HS)
- Bitcoin Traceback
- Mobile phone/encryption cracking
- Future Directions in cryptography presenting new challenges for law enforcement and the government intelligence community.
Seminar #7
16:30-17:15
SSL/TLS Interception Workshop
Presented by: Vladimir Vesely (Ph.D., Computer Science) and Jan Pluskal, Researchers, Brno University of Technology
The presentation introduces methods for intercepting TLS/SSL connections. The focus is on man-in-
middle attack employing TLS/SSL proxy and other ways how to obtain session's private keys. Speakers will outline necessary theory (including the history of SSL/TLS framework design), well-known attacks (including OpenSSL Hearthbleed, Logjam or BEAST) and industry standard tools (such as Wireshark, NetFox Detective, Fiddler Proxy and SSL-Split). The session will also include a live demonstration of MitM attack on HTTPS connections enhanced with form-logging JavaScript injection. Participants will receive free of charge access to test-bed, which consists of real devices (and their traffic) including the prototype of our hardware probe decrypting SSL/TLS on-the-fly.
Thursday, 3 June 2021
Seminar #8
13:00-14:00
Understanding "Defeating Encryption" with Quantum Computing for Non-Engineers
Presented by: Jerry Lucas, (Ph.D, Physics) President, TeleStrategies
This one hour, session is for cyber security executives and specialists who have the responsibility of assessing the lead time they have before deploying quantum safe cryptography solutions but don't have a technical background. If you believe nation state security agencies are developing quantum computing to decrypt your past and future intercepted transmission sessions, this high-level webinar should be a must attend briefing.
And to do this you need to understand how a quantum computing circuit works when designed for the sole purpose of defeating public key encryption.
Seminar #9
13:00-14:00
Top 20 Open Source Tools (OSINT) Used in Cybercrime Investigations
Presented by: Mark Bentley, Communications Data Expert, National Cyber Crime Law Enforcement, UK Police
https://register.gotowebinar.com/register/5972294686732126475
Our autonomous, end-to-end counter-drone technology solution
https://i-hls.com/archives/103732
https://web.archive.org/web/20200928203640/https://i-hls.com/archives/103732
What do drone threats, pedophile crime, terrorism, and the COVID-19 pandemic have in common? The response to all of these threats and many more is provided by the ground-breaking technologies developed by the Israeli company NSO Group.
NSO is the world leading tech company developing technological solutions, licensing software solutions to governments and law enforcement agencies to investigate and prevent terror acts, fight crime, increase public safety and save lives.
The company has excelled in identifying challenges threatening human society. This has been also demonstrated over the backdrop of the COVID-19 pandemic, by the development of FLEMING – the analytics system that enables governments to block the pandemic and return to normal through the identification of COVID-19 patients and people who came in contact with them. The company’s advanced solutions can cope with the most advanced encryption methods currently used by terrorists and pedophiles, that are now harder to monitor and track, as well as cope with drone threats, thanks to its new system – Eclypse.
The increasing availability and accessibility of affordable drones, which can be fitted with advanced offensive capabilities, has the potential to create life-threatening situations. Launched recently, Eclipse is an innovative drone defense system that helps counter rogue drones before they become a threat. The system offers a threat mitigation capability for dense urban environments, smart cities, stadiums, critical infrastructure, airports, correctional institutions, landmarks, private enterprises, and more.
This premier cyber counter-drone platform is designed to automatically detect, take over and safely land unauthorized commercial drones in a designated zone, to differ from military counter-drone solutions.
 Michel Berdah, NSO. Photo by Matania Tausig
Michel Berdah, NSO. Photo by Matania Tausig
How does Eclipse reduce risks to public safety? Michel Berdah, NSO’s VP Sales explains: “Over the past few years, the presence of drones in public spaces has become an ever-increasing threat. In the wrong hands, these unmanned aircrafts can turn into dangerous weapons. NSO identified the danger of drones being used for nefarious purposes early on and acted to develop an effective, safe and sophisticated tool that provides airtight protection from drones in public spaces and critical infrastructure facilities.”
Eclipse deploys an autonomous end-to-end cyber solution to detect activity within a designated perimeter, identify the presence of drones, take over control of the threatening drones in an “elegant” way, and land them safely right where the operator has chosen to. The system can identify friend or foe drones flown at the same airspace.
Eclipse operates automatically according to pre-defined parameters, removing the requirement for real-time decision making. Furthermore, it is designed not to jam existing communications platforms, with no impact on wireless communications and GPS signals. It is the only drone defense system that is FCC, CE compliant.
With its distributed architecture, the platform seamlessly connects to existing infrastructure. This best-in-class technology has been developed in-house by the company’s seasoned and knowledgeable development team which brings to the table a decade of experience in the defense technology realms.
“Eclipse is already deployed in dozens of countries, helping security and enforcement forces save lives. We look forward to working with future partners around the world,” Michel Berdah points out.
NSO’s wide array of products is used successfully in various countries around the world serving intelligence agencies and governments in life-saving missions, including terrorism prevention, breaking up child exploitation, assisting search and rescue (SAR) teams in locating survivors trapped under collapsed buildings, helping governments plan lockdown exit strategies, and more.
As Michel Berdah concludes, “I can proudly say that the NSO’s technological capabilities defeat world evil, day by day, night by night.”
iHLS INNOFENSE – Innovation program for technological startups in the civilian and security sector, which will be operated by iHLS in collaboration with the Ministry of Defense and MAF’AT
Israel Ministry of Defense and iHLS collaborate in iHLS INNOFENSE innovation center – “an innovation program for technological projects in the civilian and security sector.” The program is designed to strengthen the links between the civilian and defense markets via the collaborative development of the technologies, thus advancing and improving their integration in both markets.
Within the framework of the program, an innovative connection model is applied for the first time vis a vis the startup companies. The model led by the Israel Ministry of Defense Chief Economist enables the entrepreneurs to operate with ultimate flexibility and accessibility to the Ministry of Defense and the IDF. During the first stage of the program, several projects will be recruited for a six-month period, and each project will receive a NIS 200,000 grant, in addition to support from the Innovation Center.
Within the framework of the Innovation Center, the entrepreneurs receive from each iHLS all the services required for the acceleration and development of the startup, including business mentoring. The company supports the projects from the stage of technological proof of concept, business development, penetration to relevant markets, legal advice, and networking for further investments in the future. They will be joined by coaches and mentors, R&D representatives from MAF’AT (Administration for the Development of Weapons and Technological Infrastructure) and the relevant arms.

iHLS INNOFENSE program is designed for projects with dual-use technologies (civilian and security) in order to enable their future expansion to other markets. The Ministry of Defense will be able to use the information for the evaluation of the technology but will not enter as a shareholder or with rights regarding the companies’ intellectual property.
Applications submission until September 30, 2019
The following challenges interest the iHLS INNOFENSE Innovation Center:
- Urban navigation – technologies for precision navigation at the urban space without dependency on GPS or communications
- Anomaly detection – in autonomous systems
- Smart Campus – the integration of user experience technologies and decreasing of dependency on human resources
- Predictive maintenance – solutions for the detection and prediction of failures in military systems
- Unmanned systems – civilian solutions and adjustment to operational and logistical missions
- Computerized image processing – automatic analytics capabilities of images and the identification of structure features on the image
- Predicting aerial activity in a specific space via the integration of military and civilian databases
- Text analysis and conclusion – the extraction of knowledge accumulated in written investigations
- The identification of process influences – understanding the influence of IT systems failure on operational processes
- Information security in a geographic perimeter – defense from information leaks in geofencing by the negation of mobile devices capabilities
- Energy efficiencies
- Storage and retrieval systems
- Other
For more details and application to iHLS INNOFENSE
Instead of Saying IDF Say Israel Robot Army: Far-Reaching Vision or
Realistic Forecast?
A US Air Force project is designed to build data links that enable semi-autonomous weapons to ‘swarm’ a target. The new munitions being designed under the Air Force Research Laboratory’s Golden Horde project use data links to communicate, choose targets (based on pre-programmed algorithms) and then coordinate strikes against an array of targets, independently from the human pilot.
In a flight demo held Dec. 15, the AFRL’s prototype ‘swarming’ munitions failed to hit their targets in their first flight demo. However, experts see the potential for networked, autonomous munitions to eventually equip America’s entire fighter fleet.
“Salvos of collaborative weapons that can share target information and autonomously coordinate their strikes after launch could help maximize target damage and compensate for weapons lost in flight due to enemy defenses or other factors,” explains Mark Gunzinger, director of future programs at the Mitchell Institute. “This would enable the U.S. military to use smaller salvos of weapons to achieve desired effects in the battlespace compared to larger salvos of non-collaborative weapons that must be independently targeted/retargeted by human operators.”
According to breakingdefense.com, the effort involves two different weapon systems — the Collaborative Small Diameter Bomb I (CSDB-I) and the Collaborative Miniature Air-Launched Decoy (CMALD).
The demo involved the release of two CSDBs from an F-16, the AFRL release said. CSDBs, lab explained, are “Small Diameter Bombs that have been modified with a collaborative autonomy payload” developed by AFRL and Scientific Applications & Research Associates (SARA).
AFRL said they were very pleased with the results, “The team saw good performance from the networked collaborative sub-systems and understands the root cause of the weapons not impacting the desired targets. We anticipate readiness for the next flight test.”
AFRL explained that during the demo the “CSDBs quickly established communication with each other and their seekers detected a GPS jammer” and using pre-defined rules of engagement pre-loaded into the system, “determined that the jammer was not the highest priority target. The weapons then collaborated to identify the two highest priority targets. However, due to an improper weapon software load, the collaboration guidance commands were not sent to the weapon navigation system. Without the updated target locations, the weapons impacted a fail-safe target location.”
iHLS TV -AUS&R BROADCAST 2020-Yair Ramati -HIGH NOON - Turkish UAV's takes down Russian Pantsir
- https://www.youtube.com/channel/UC1iOIybOg7fiHCbacRjc18w
- https://ausr-broadcast.i-hls.com/plenary/high-noon-turkish-uavs-take-down-russian-pantsir/
2021 ISS World Europe - Lead Sponsor
 |
Our company is a global leader in the world of cyber-intelligence, data acquisition and analysis. Our portfolio of high-end operational and analytical tools is shaped by years of focused research, development, and operational experience. The product suite is used to investigate and prevent crime and terror as well as preserve national security. Since 2009, our mission has been to help select intelligence organizations, law enforcement agencies, and military forces with the best strategic, tactical, and analytic solutions required to ensure the success of their operations. Our product portfolio, with its target centric and service provider independent technology, enables government agencies to identify targets, locate their whereabouts, and covertly gather valuable intelligence without compromising user service or experience. |
|---|
ISS World 2021 Europe -- Associate Sponsors
 |
AdaptiveMobile Security is the world leader in cyber-telecoms security, powered by our core expertise and foundation in security with a unique managed real-time mobile network enforcement solutions for mobile network and messaging security. We provide security solutions and intelligence services to mobile carriers, communications platform providers, governments and regulators. |
|---|---|
 |
Advanced Systems is a provider in Comint solutions ; Advanced Systems provide lawful interception system for voice and IP. We are specialized in handling very big data streams ( several 100GBit/s), being able to retrieve any interesting information thanks to our embedded "Analytics Intelligence" and our Intelligent Data Retention System. Advanced Systems can provide also massive passive GSM off the air interception system. |
 |
Allot (NASDAQ, TASE: ALLT), founded in 1996, is a world leader in network intelligence and security solutions for Regulators, Government Agencies, Communications Service Providers, and Enterprises. We empower customers to turn regulations into actionable network policies that ensure national cybersecurity. Allot’s digital enforcement solutions transform network data into actionable intelligence that safeguards countries, secures networks, and protects users. |
 |
AREA, is the Italian leading technology Industry and provider of Unconventional Communication and IP Info-Intelligence solutions.AREA provides an “end to end” Dual Use Info-Intelligence CC forHLS/HLD scenarios; satisfying Government Agencies’ need to securely and effectively gather precious information to contrast menaces to Citizen’s security and prevent digital attacks. |
 |
ATIS systems is a German, private held company offering first-class complete solutions for legal interception, mediation, data retention, and IT forensics. Belonging to the world leaders in technology in this field, we have been developing high performance systems for over 70 years. Clients all over the world have placed their trust in our high-quality standards, our innovative technologies, and our absolute reliability. |
|
BAE Systems help nations, governments and businesses around the world defend themselves against cybercrime, reduce their risk in the connected world, comply with regulation, and transform their operations. We do this using our unique set of solutions, systems, experience and processes - often collecting and analysing huge volumes of data. |
|
|
Cellebrite’s integrated, end-to-end Digital Intelligence Platform is revolutionizing digital forensics and offers unparalleled access to the largest assortment of digital devices and cloud data and solutions that minimize the need for manual review of digital data. The result is actionable data that reduces the time needed to make the right decision. Cellebrite sets the standard every day by providing digital forensics solutions that help make this a safer world. |
|
 |
ClearTrail Technologies is a leading provider of Communication Analytics Solutions that derives intelligence from data unlike ever before. As the threat landscape is changing rapidly, conventional monitoring approaches are getting obsolete and government agencies & enterprises need a new way of monitoring and analysing the communication networks. ClearTrail has come up with path breaking solutions that are designed to analyse even dark communication in massive data sets and connect the dots to create a single view of “Person of Interest”. Our solutions are designed to transform the investigation paradigm from reactive to proactive, empowering our clients to perceive emerging threats & reveal the potential suspects behind it. |
 |
Cobwebs Technologies is a worldwide leader in web intelligence. Our innovative solutions are tailored to the operational needs of national security agencies and the private sector, identifying threats with just one click. Our exclusive technology extracts targeted intelligence from big data using the latest machine learning algorithms, automatically generating intelligent insights. |
 |
CY4GATE is a unique, pioneering Italian Company with a portfolio of proprietary Lawful interception, Cyber Intelligence and Cyber Security software solutions. The CY4GATE Cyber-Intelligence products’ portfolio is constituted by an integrated suite for LAWFUL INTERCEPTION and VIRTUAL HUMINT activities and by the DSINT, AUGMENTED DATA ANALYTICS & INTELLIGENCE platform. The suite for lawful interception and virtual humint is based on state-of-the-art software solutions entirely developed by CY4Gate and have been fully integrated to support a coordinated operation able to approach and acquire information from a specific target. |
 |
D-Fend Solutions AD Ltd. is a global leader in counter-drone solutions for urban environments, perimeter security and mobile assets protection. D-Fend’s EnforceAir is an autonomous, non-jamming, non-spoofing, and non-kinetic counter-drone system, designed to detect & take control over rogue commercial drones, and land them safely in a designated safe zone. |
 |
Founded in 2003, DEVERYWARE is the European expert in investigation technologies and global security services, committed to serving the security of States, businesses and communities through innovative digital technologies and high value-added solutions. The group's offer, together with its subsidiaries’ offer – OAK BRANCH, TRACIP and RESILIENCY, covers forensic investigation, data analysis, real-time geolocation platforms, big data, crisis management and the new generation emergency call. |
 |
Elbit Systems Ltd. is an international high technology company engaged in a wide range of defense, homeland security and commercial programs throughout the world. The Company, which includes Elbit Systems and its subsidiaries, operates in the areas of aerospace, land and naval systems, command, control, communications, computers, intelligence surveillance and reconnaissance (“C4ISR”), unmanned aircraft systems, advanced electro-optics, electro-optic space systems, EW suites, signal intelligence systems, data links and communications systems, radios and cyber-based systems. The Company also focuses on the upgrading of existing platforms, developing new technologies for defense, homeland security and commercial applications and providing a range of support services, including training and simulation systems. |
 |
Feedback Italia specializes in designing and developing cyber security solutions and systems. Focusing on developing pioneering audio and video communication solutions from its early establishment, Feedback Italia has been increasingly committed to implement an unprecedented level of communication security. The company R&D department never stops the pursuit for the state-of-the-art encryption technology, to offer devices, software, and services all working together to keep leading global businesses and governments safe and secure. |
 |
FinFisher solutions help government law enforcement and intelligence agencies to identify, locate and convict serious criminals. With innovative products, tailor-made solutions and end-to-end services FinFisher closes the gap in traditional investigative methods. Its portfolio allows governments to gain access to protected, offline information and relevant web-based communication channels. |
 |
Gamma Group is an international manufacturer of surveillance & monitoring systems with technical and sales offices in Europe, Asia, the Middle East and Africa. We provide advanced technical surveillance, monitoring and Media Mining/OSINT solutions, advanced government training, as well as international consultancy to National and State Intelligence Departments and Law Enforcement Agencies. |
 |
Having a strong footprint in Germany since 2000, INNOSYSTEC is a market leading provider of Big Data Analysis solutions for intelligence authorities worldwide. Our product SCOPE provides a unique platform for correlation and analysis of billions of data sets from multiple feeds. Indifferent of strategic or tactical challenges: SCOPE enables you to access all data you need to predict and prevent. Our solutions contribute to the protection of human lives in the everyday life. |
 |
IPS is an Italian high-tech company with 30 years’ experience in the design and delivery of "turnkey" solutions for Communication Monitoring and Analysis. IPS solutions are specifically designed for Homeland Security Departments and Intelligence Agencies that need to intercept, collect and deep analyze heterogeneous data such as phone calls, Internet traffic, data coming from electronic surveillance devices and third parts databases. The IPS monitoring platforms are used today in around 20 countries in 4 continents: Europe, Latin America, Africa and Asia. |
 |
JENOVICE was established by the CEO of the company, a former head of intelligence and investigations of a government services. The vision was to provide tactical solutions in the field of Offensive Cyber Security. The VP R&D of the company is an ex special-ops combat solider with experience in tactical operations and 10 years of experience in IT, software engineering and research. |
 |
MEMENTO LABS, part of InTheCyber Group, is the new top-notch player in the Intelligence ground. Memento Labs raises the bar of the state-of-the art to a new level, offering products able to fulfill LEA’s and Security Agencies’ highest expectations. Our Mission is the development of advanced tools and solution to outperform in the Hybrid Warfare era. Memento Labs commitment is to continuously innovate to be at the forefront of finding solutions. |
 |
Established by a group of elite intelligence and operations professionals, Merlinx has developed groundbreaking intelligence acquisition solutions. Merlinx enables operators to be in the right place at the right time, in order to identify and acquire critical cyber intelligence. Merlinx is a privately held company specializing in tailor-made innovative active cyber intelligence solutions. |
 |
One-stop shop for the full range of high-end storage, IT and network solutions. Everything from small hand-held devices, workstations and servers, right up to fool-proof high performance scalable Cluster Labs.
|
 |
NeoSoft is an independent Swiss company with more than 20 years of expertise in the field providing high quality mobile communication products including: GSM/UMTS/LTE IMSI catcher with Public Number detection, GSM/UMTS/LTE Active Monitoring solution, GSM Passive Monitoring with A5/3 support, Wi-Fi Monitoring supporting 2.4 GHz and 5 GHz, IMSI catcher detection, Wi-Fi Monitoring detection, Selective Wi-Fi jamming solution |
 |
Polaris Wireless is the global leader in providing high-accuracy, software-based wireless location solutions for wireless operators, law enforcement/government agencies and location-based application companies. Since 2003, Polaris Wireless has successfully completed 49 global deployments for public safety, national security and commercial LBS applications. Polaris Wireless is the recipient of the prestigious Frost & Sullivan “2011 and 2014 Enabling Technology of the Year” award for its patented Wireless Location Signatures technology that uniquely enables accurate indoor, outdoor and vertical location and accurate mass location. |
 |
Rayzone Group is a developer and provider of cyber and intelligence solutions for intelligence and law enforcement agencies worldwide, based on comprehensive methodology, which provides cutting edge intelligence gathering and analysis capabilities. Rayzone’s suite of systems include sophisticated gathering and analysis solutions to some of the most pressing challenges that government agencies face today. |
 |
RCS provides highly scalable, secure and comprehensive lawful interception and digital surveillance systems to approved Governments and Agencies enabling them to digitally collect and see a deep and rich intelligence picture of their persons of interest and to visualise their timings, intentions and capabilities. Collection – Decoding – Processing - Correlation – Analysis. |
 |
For more than 80 years, Rohde & Schwarz has stood for quality, precision and innovation in all fields of wireless communications. The group relies on its expertise based on 20 years of experience in IT and network security. All Rohde & Schwarz development, sales and service activities focus on the customer. |
 |
The French company SUNERIS develops monitoring and control solutions for telecom networks. Our systems are used by government entities to comply with telecom regulations and support civil safety missions: people rescue, antiterrorism, border surveillance…. The modularity, reliability and furtivity of our solutions allow to fit your operational needs. |
 |
trovicor is a world leader in lawful intelligence technology, providing end-to-end monitoring and intelligence solutions to more than 35 governments across the globe. With 20+ years’ experience of collaborating with governments worldwide, trovicor’s solutions are a powerful tool proven to help governments protect their citizens against the threat of criminal activity and safeguard national security. With these tools, we help criminal investigators detect traces of criminal activity, identify suspects and transform this intelligence into reliable and accurate evidence to be used in court. |
 |
Ultra Information Solutions is a global leading expert in target-centric intelligence. Ultra´s innovative technology is capable of identifying a Target's Digital Footprint Directly or via Mass Monitoring based on a single seed and generating unique and valuable insights that offer a critical advantage in an era of globalization, connectivity and anonymity. |
 |
Utimaco´s carrier-grade systems enable real-time monitoring and long-term data retention in public telecommunication networks since 1994. Utimaco is the preferred partner of many of the world’s leading network equipment vendors. With around 300 installations in over 90 countries, Utimaco is one of the leading global suppliers in the Lawful Interception and Data Retention market. |
 |
Verint is a leading global provider of security and intelligence data mining software. We leverage our deep domain expertise to create solutions that prevent and neutralize terror, crime and cyber-attacks. Our broad Intelligence-Powered Security™ portfolio empowers security organizations with crucial insights that enable them to take action against evolving threats. |
 |
VLATACOM INSTITUTE is a professional partner for Government security in the following technical fields: Secure information and communication technology, Border control, Applied mathematics and electronics with cryptography features, Intelligent signal processing etc. For past two decades we are among leading Serbian manufacturers and system integrators in these fields recognized world-wide. |
 |
Voyager Labs is the leader in artificial intelligence for analyzing human behavior from the vast ocean of unstructured data. Its unique technology searches, aggregates and fuses billions of publicly available data points and human behavior indicators from multiple data sources, intelligently processing and analyzing them to provide deep, actionable insights which enhance and accelerate investigations and intelligence. |
|
Wintego’s core expertise is in developing cyber intelligence solutions for government, law enforcement, military, and intelligence agencies. The company’s multi-disciplinary team of highly experienced cyber professionals is focused exclusively on providing advanced cyber solutions that address the needs of the real world, today and in the long term. Over the past years, Wintego’s solutions have been deployed by numerous government agencies around the globe. |
|
 |
WiSpear provides end-to-end WiFi surveillance solutions for the intelligence, homeland security and public safety markets. WiSpear’s products are based on a disruptive long range, directional, beamforming WiFi technology, and on unique and leading SW applications. |
ISS World Europe 2021 - Exhibiting Sponsors
https://alphasecurityanddefense.com/our-partners/
http://www.info-clipper.com/en/company/israel/q-cyber-technologies-ltd.ild9xly9j.html
https://efile.fara.gov/docs/6170-Informational-Materials-20201117-767.pdf
https://opencorpdata.com/lei/222100KKW3GGPGATJ296
https://tspace.library.utoronto.ca/bitstream/1807/96793/1/Report%23117--Reckless%20VII.pdf
https://citizenlab.ca/2019/03/nso-spyware-slain-journalists-wife/
https://www.lcpdfr.com/discover/
https://tspace.library.utoronto.ca/bitstream/1807/96793/1/Report%23117--Reckless%20VII.pdf
This report is Part 8 of a series on the abuse of NSO Group’s spyware in Mexico
Part 1: Bittersweet: Supporters of Mexico’s Soda Tax Targeted With NSO Exploit Links
Part 2: Reckless Exploit: Mexican Journalists, Lawyers, and a Child Targeted with NSO Spyware
Part 3: Reckless Redux: Senior Mexican Legislators and Politicians Targeted with NSO Spyware
Part 4: Reckless III: Investigation Into Mexican Mass Disappearance Targeted with NSO Spyware
Part 5: Reckless IV: Lawyers For Murdered Mexican Women’s Families Targeted with NSO Spyware
Part 6: Reckless V: Director of Mexican Anti-Corruption Group Targeted with NSO Group’s Spyware
Recent Background: Da Vinci and Mamfakinch.com
On Friday the 13th of July 2012, the Moroccan citizen media and journalism project Mamfakinch3 was targeted by an electronic attack that used surveillance malware. Mamfakinch.com, a website that is frequently critical of the Moroccan government, received a message via their website directing recipients to a remote webpage:
The text, which hints at a sensitive scoop or lead translates roughly as “please don’t mention my name and don’t say anything at all [about me] I don’t want to get mixed up in this”.
The logs of the website reveal this message was sent from Moroccan IP space:
41.137.57.198 – – [13/Jul/2012:20:48:46 +0100] “GET /wp-content/plugins/wp-cumulus/tagcloud.swf?r=8659047 HTTP/1.0” 200 34610 “https://www.mamfakinch.com/nous-contacter/” “Mozilla/5.0 (Windows NT 6.1; WOW64; rv:13.0) Gecko/20100101 Firefox/13.0.1”
41.137.57.198 – – [13/Jul/2012:20:48:47 +0100] “GET /nous-contacter/?_wpcf7_is_ajax_call=1&_wpcf7=2782 HTTP/1.1” 200 9886 “https://www.mamfakinch.com/nous-contacter/” “Mozilla/5.0 (Windows NT 6.1; WOW64; rv:13.0) Gecko/20100101 Firefox/13.0.1”
41.137.57.198 – – [13/Jul/2012:20:50:08 +0100] “POST /nous-contacter/ HTTP/1.1” 200 139 “https://www.mamfakinch.com/nous-contacter/” “Mozilla/5.0 (Windows NT 6.1; WOW64; rv:13.0) Gecko/20100101 Firefox/13.0.1”
41.137.57.198 – – [13/Jul/2012:20:50:12 +0100] “GET /nous-contacter/ HTTP/1.1” 200 9887 “https://www.mamfakinch.com/nous-contacter/” “Mozilla/5.0 (Windows NT 6.1; WOW64; rv:13.0) Gecko/20100101 Firefox/13.0.1”
41.137.57.198 – – [13/Jul/2012:20:50:14 +0100] “GET /nous-contacter/?_wpcf7_is_ajax_call=1&_wpcf7=2782 HTTP/1.1” 200 9888 “https://www.mamfakinch.com/nous-contacter/” “Mozilla/5.0 (Windows NT 6.1; WOW64; rv:13.0) Gecko/20100101 Firefox/13.0.1”
The IP from which the targeting message was uploaded (41.137.57.198) is from a Moroccan range dedicated to mobile 3G Internet users in the capital Rabat and its surroundings:
netname: INWI-PDSN1-Rabat001
country: MA
admin-c: AN2-AFRINIC
tech-c: AN2-AFRINIC
The page, found at http://freeme.eu5.org/scandale%20(2).doc prompted the user for the installation of malicious java, file, “adobe.jar”:
This file then facilitated the installation of a multi-platform (OSX and Windows) backdoor.
Length Date Time Name
——— ———- —– —-
253 2012-07-09 14:33 META-INF/MANIFEST.MF
374 2012-07-09 14:33 META-INF/SIGNAPPL.SF
888 2012-07-09 14:33 META-INF/SIGNAPPL.DSA
0 2011-09-15 11:07 META-INF/
3853 2011-09-15 11:07 WebEnhancer.class
1043456 2012-07-09 16:33 win
993440 2012-07-09 16:33 mac
——— ——-
2042264 7 files
In the contents of the .jar you can see files called “win” and “mac” which correspond to Windows and OSX backdoors respectively:
10fa7fa952dfc933b96d92ccd254a7655840250a787a1b4d9889bf2f70153791 mac
The Windows backdoor contains a variety of clear-text strings which are found in the SSH-client, “Putty”. The OSX version of the backdoor, however, contains what appear to be to debug strings referencing the name of the developer,
‘Guido’:
Users/guido/Projects/driver-macos/
/Users/guido/Projects/driver-macos/mchook.cC:/RCS/jlc3V7we.app
C:/RCS/DB/temp
C:/RCS/DB/temp/1341jlc3V7we.app
C:/RCS/DB/temp$
Execution of the Windows backdoor writes the following files to disk:
C:\DOCUME~1\ADMINI~1\LOCALS~1\jlc3V7we\eiYNz1gd.Cfp
C:\DOCUME~1\ADMINI~1\LOCALS~1\jlc3V7we\t2HBeaM5.OUk
C:\DOCUME~1\ADMINI~1\LOCALS~1\jlc3V7we\WeP1xpBU.wA-
C:\DOCUME~1\ADMINI~1\LOCALS~1\jlc3V7we\6EaqyFfo.zIK
C:\DOCUME~1\ADMINI~1\LOCALS~1\jlc3V7we\lUnsA3Ci.Bz7
The file ‘ZsROY7X.-MP’ appears to provide the main backdoor functionality:
It is executed via rundll32 and the following registry entry created to ensure persistence:
Processes such as iexexplorer.exe and wscntfy.exe are infected.
Examination of loaded modules for “wscntfy.exe” reveals:
C:\WINDOWS\system32\winhttp.dll
C:\WINDOWS\system32\ws2_32.dll
C:\WINDOWS\system32\ws2help.dll
C:\WINDOWS\system32\ole32.dll
C:\WINDOWS\system32\oleaut32.dll
C:\WINDOWS\system32\imm32.dll
The backdoor has been identified as a variant of a
commercial backdoor sold by the Italian Company “Hacking Team”
First identified by Russian Antivirus company Dr Web on July 25th, 2012, the backdoor has been called “Remote Control System,” “Crisis” and “DaVinci”.
The Hacking Team Remote Control System (RCS) is described in a leaked copy of their promotional literature as:
“A stealth, spyware-based system for attacking, infecting and monitoring computers and smartphones. Full intelligence on target users even for encrypted communications (Skype, PGP, secure web mail, etc.)”4
The Hacking Team public website stipulates that their technology is sold only to a restricted customer base:
“…we provide effective, easy-to-use offensive technology to the worldwide law enforcement and intelligence communities.
What Can You Do?
All iPhone owners should update to the latest version of iOS (9.3.5) immediately. If you’re unsure what version you’re running, you can check it yourself by tapping Settings > General > About > Version.
Citizen Lab agrees with Apple that users should avoid opening or downloading items from messages and websites unless they are certain that they come from a legitimate, trusted source. If you uncertain about the source, you should not click the link or open the file. If you believe you have been the victim of a targeted attack, should consider sharing it with a trusted expert. If you suspect you have been the target of this attack, please contact the Citizen Lab at info@citizenlab.org.
Zero-day exploits are expensive and rare, especially one-click remote jailbreak exploits for iPhones, like the Trident. Such exploits can fetch hundreds of thousands or even a million dollars. While Citizen Lab research has shown that many state-sponsored spyware campaigns against civil society groups and human rights defenders use “just enough” technical sophistication, coupled with carefully planned deception, the attack on Mansoor demonstrates that not all threats follow this pattern.
This is the third time Mansoor has been targeted with “lawful intercept” spyware; Mansoor was targeted in 2011 with spyware from FinFisher (based in Germany and the UK), in 2012 with spyware from Hacking Team (based in Italy), and now in 2016 with what appears to be spyware from NSO Group (based in Israel and reportedly owned by a US firm). That the companies whose spyware was used to target Mansoor are all owned and operated from democracies speaks volumes about the lack of accountability and effective regulation in the cross-border commercial spyware trade.
While these spyware tools are developed in democracies, they continue to be sold to countries with notorious records of abusive targeting of human rights defenders. Such sales occur despite the existence of applicable export controls. For example, Israel’s export regime incorporates the dual-use technology controls of the Wassenaar Arrangement, including those related to “intrusion software.” As such, NSO Group would presumably be required to obtain a license to export its products to the UAE. If NSO Group did submit a license application, the human rights abuses perpetrated by the UAE, including the misuse of “lawful intercept” capabilities, must not have outweighed authorities’ other motivations to approve the export.
Clearly, additional legal and regulatory scrutiny of the the “lawful intercept” market, and of NSO Group’s activities in relation to the attacks we have described, is essential. Citizen Lab and others have repeatedly demonstrated that advanced “lawful intercept” spyware enables some governments and agencies, especially those operating without strong oversight, to target and harass journalists, activists and human rights workers. If spyware companies are unwilling to recognize the role that their products play in undermining human rights, or address these urgent concerns, they will continue to strengthen the case for further intervention by governments and other stakeholders.
Note: We are not releasing the malicious files at this time to protect the integrity of ongoing investigations.