

The third lesson of smart phone’s security
The comprehensive guide of  Android
Android
Praise to Allah the Bestower of honor and victory, the Humiliator of al-shirk with His vanquish, guide the things by his authority, inveigled the unbelievers by his wiliness, estimated the days countries by
His justice, Gave the good health to the pious by His grace. Pray and peace on (the one whom Allah tops Islam with his sword), on his family, friends and who follow them with beneficence to the Day of Judgment
Brief on  and How does it work
and How does it work

-------------------------------------------
What is  ?
?
-------------------------------------------
 has been developed to secure the anonymous communication, privacy and security for the user’s activities on the internet, the program links the users with the
has been developed to secure the anonymous communication, privacy and security for the user’s activities on the internet, the program links the users with the  web, it contain group of interference series which make connect the operation done through these series to get complete privacy and security to the users whether in recording their movement on the internet or the websites they visit .it also protect them from tracing , identify their divinity and the operation of spying that could be done by persons or companies or government.
web, it contain group of interference series which make connect the operation done through these series to get complete privacy and security to the users whether in recording their movement on the internet or the websites they visit .it also protect them from tracing , identify their divinity and the operation of spying that could be done by persons or companies or government.
-----------------------------------------------------------
What do “node” and  web mean?
web mean?
-----------------------------------------------------------
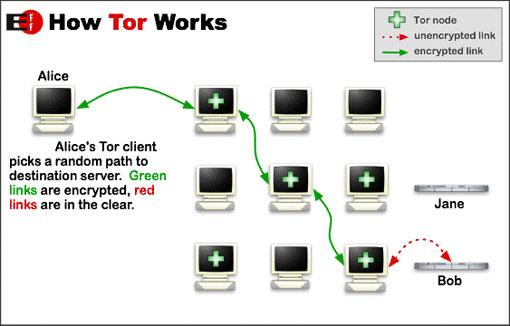
 web is large group of personal devices run by volunteers all over the world these devices named “node”
web is large group of personal devices run by volunteers all over the world these devices named “node”
A node chooses by  randomly to pass every connection, each connection contains 3 nodes entrance node, middle node and the exit node. This way doesn’t allow any person to trace your connection on the internet or websites and services you visit on the internet and also prevent identifying your geographic location.
randomly to pass every connection, each connection contains 3 nodes entrance node, middle node and the exit node. This way doesn’t allow any person to trace your connection on the internet or websites and services you visit on the internet and also prevent identifying your geographic location.
The entrance node: in  , indicate your geographical location, it doesn’t know the data that been sent because it encrypted before entrance.
, indicate your geographical location, it doesn’t know the data that been sent because it encrypted before entrance.
The middle node: it doesn’t identify any information like (your geographical location, the data you sent, and the website you will visit); this node used to receive data from entrance node and passes it to the exit node.
Exit node: it decodes the data then passes it to the website. So the exit node identify the website you will visit and the data you sent to passes it to the website, but if you used  in a website which encrypted Https the exit node will identify the website you want to visit only, the data will decode in the website that you visited.
in a website which encrypted Https the exit node will identify the website you want to visit only, the data will decode in the website that you visited.
To download  for Android from
for Android from  store press here or the direct download prees here.
store press here or the direct download prees here.

Recently  doesn’t work on android devices except by using the root terms of references but now VPN service added which encrypt the connection of the internet by using
doesn’t work on android devices except by using the root terms of references but now VPN service added which encrypt the connection of the internet by using web.
web.
To activate this service press on (Apps) in the previous picture, then press Activate.
Notice a key will appear at the notification toolbar, it means the application works.
Imp. Note: Apps service still trail, it doesn’t work on all the devices, maybe it stop automatically, and we don’t advice to use it in hiding because it designed to exceed the firewalls and the filters.
Press here to go to the Application settings

-------------------------------------------------------------------
The first stage: the General Settings
-------------------------------------------------------------------
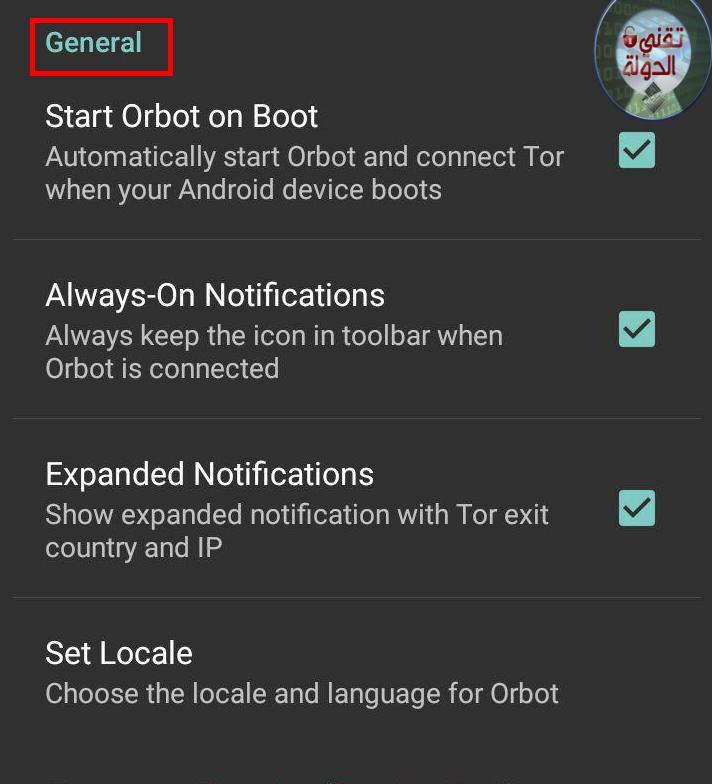
1) Start Orbit on Boot Automatically start Orbot and connect  when your Android device boots
when your Android device boots
2) Always-On Notification Always keep the icon in toolbar when Orbot is connected
3) Expanded Notifications Show expanded notification with  exit country and IP
exit country and IP
4) Set locateTo change the language of the application but after you choose the new language, logout from the application then open it again.
-------------------------------------------------------------------
The second stage: Transparent Proxying
-------------------------------------------------------------------
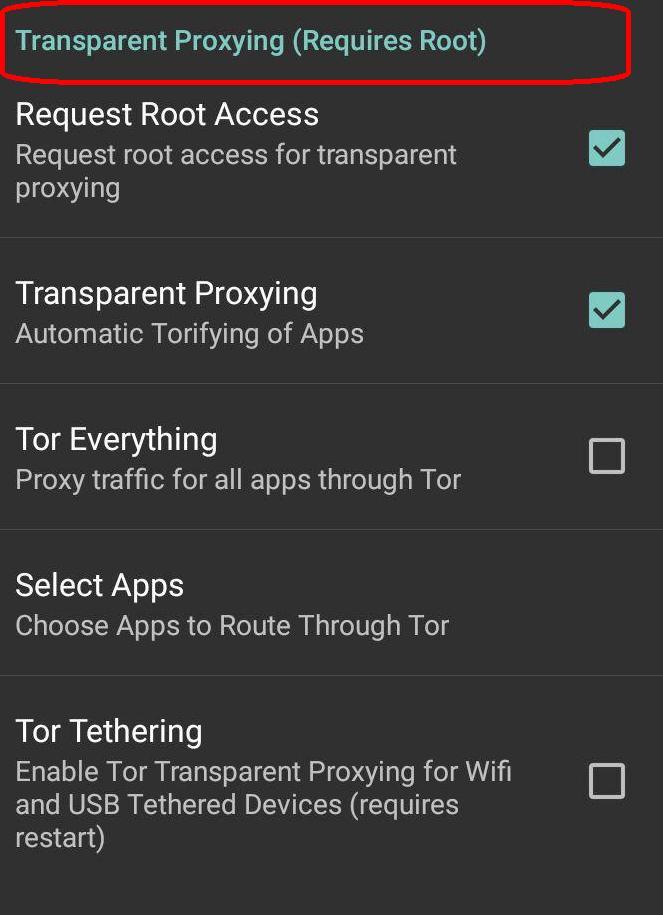
1) Request Root Access
Request root access
2) Transparent Proxing
Automatic torifying of Apps
3) Everything
Everything
Proxy traffic for all apps through
Note: you don’t need to add manual proxy to the application in this option
4) Select application
Choose Apps to route through
5)  Tethering
Tethering
Enable tor transparent proxying for Wi-Fi and USB tethered devices (requires restart)
Imp Note: by activating Transparent Proxying it encrypts all connections of the applications, and you don’t need to add manual proxy to the application like Twitter and Firefox.
--------------------------------------------------------------
The Third Stage: Node configuration
--------------------------------------------------------------
Note: we explained before the node and its types, we can identify which country your data and connection passes through it, by adding country’s shortcut to each node.
1) Entrance nodes
This option tells Tor that it has to pass only from the entrance and middle node that exist in the specific countries.
This line below has shortcuts to many countries; European and Australian are better in protecting the privacy like Switzerland Romania and Australia.
Copy and paste the line in the Entrance Nodes
2) Exit Nodes: this option tells  that it has to pass through the exit node at the specific countries.
that it has to pass through the exit node at the specific countries.
Add the previous list of shortcuts in the Exit Nodes.
3) Exclude Nodes: this option tell  it had to bypasses from Exit nodes that exists in the specific countries
it had to bypasses from Exit nodes that exists in the specific countries
Add these countries to the option.
These shortcuts of America, US, Russia, Syria, Egypt, Saudi and Tunisia, so add your country to these countries to prevent the connection to pass through it.
This link has shortcuts for all countries press here
4) Strict Nodes: this option related to the Exclude nodes, you could activate or inactivate it, if you activate it your connection won’t pass through the countries you added to the exclude nodes.
--------------------------------------------------------
The fourth Stage: Adding Bridges
--------------------------------------------------------
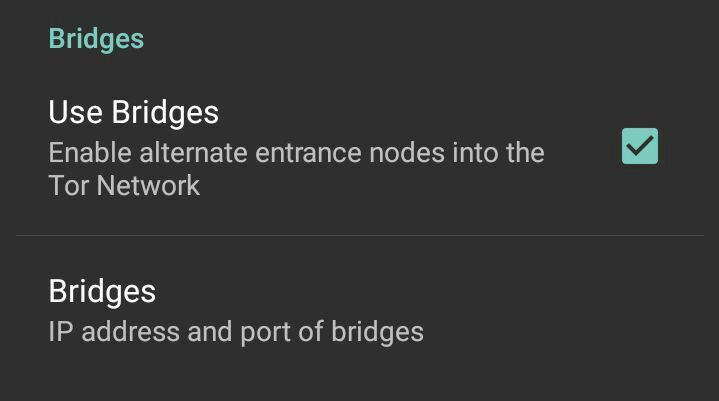
1) Use bridges : activate the bridge , the bridge is a group of nodes connect to the Tor web, it works as entrance node, it couldn’t be blocked from the service provider or the government
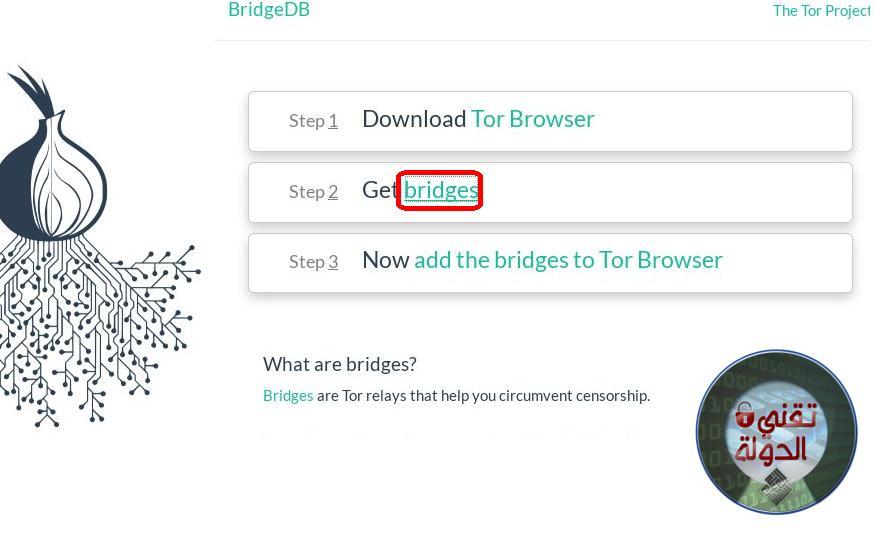
2) Bridges : Add the bridge by going to the link
Then follow the following steps
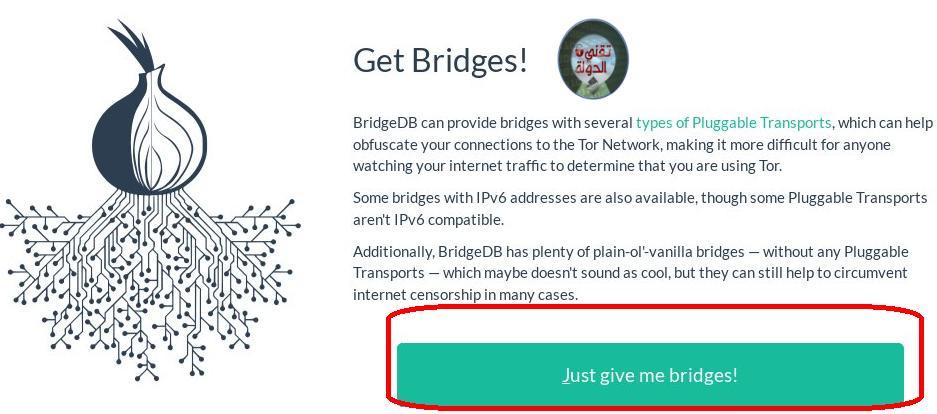
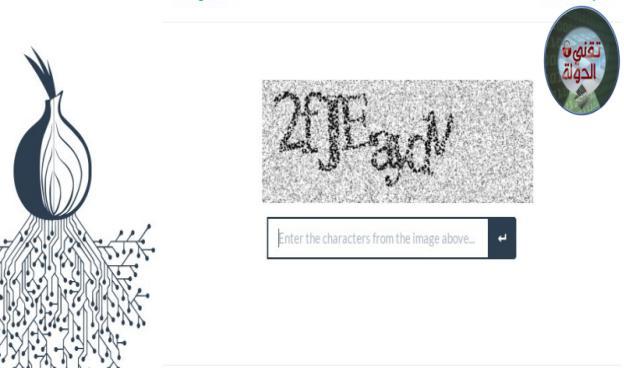
In the next picture write the code in the picture then press on the arrow
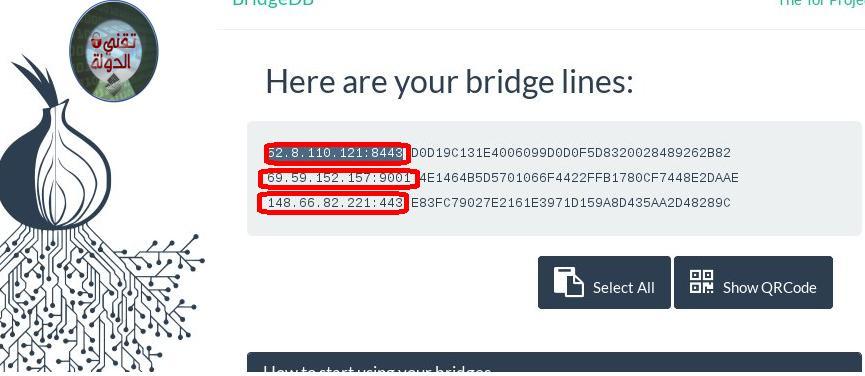
In the next picture the red numbers are the bridges of the orbit application copy the bridge and paste it in the application.
-------------------------------------------------------------------
Don’t forget us by duaa
Written by: Technique the Islamic State

@SOFTWARE_ENG

 Android
Android and How does it work
and How does it work
 ?
? has been developed to secure the anonymous communication, privacy and security for the user’s activities on the internet, the program links the users with the
has been developed to secure the anonymous communication, privacy and security for the user’s activities on the internet, the program links the users with the  web, it contain group of interference series which make connect the operation done through these series to get complete privacy and security to the users whether in recording their movement on the internet or the websites they visit .it also protect them from tracing , identify their divinity and the operation of spying that could be done by persons or companies or government.
web, it contain group of interference series which make connect the operation done through these series to get complete privacy and security to the users whether in recording their movement on the internet or the websites they visit .it also protect them from tracing , identify their divinity and the operation of spying that could be done by persons or companies or government.
 web mean?
web mean? web is large group of personal devices run by volunteers all over the world these devices named “node”
web is large group of personal devices run by volunteers all over the world these devices named “node” randomly to pass every connection, each connection contains 3 nodes entrance node, middle node and the exit node. This way doesn’t allow any person to trace your connection on the internet or websites and services you visit on the internet and also prevent identifying your geographic location.
randomly to pass every connection, each connection contains 3 nodes entrance node, middle node and the exit node. This way doesn’t allow any person to trace your connection on the internet or websites and services you visit on the internet and also prevent identifying your geographic location. , indicate your geographical location, it doesn’t know the data that been sent because it encrypted before entrance.
, indicate your geographical location, it doesn’t know the data that been sent because it encrypted before entrance. in a website which encrypted Https the exit node will identify the website you want to visit only, the data will decode in the website that you visited.
in a website which encrypted Https the exit node will identify the website you want to visit only, the data will decode in the website that you visited. for Android from
for Android from  store press here or the direct download prees here.
store press here or the direct download prees here. doesn’t work on android devices except by using the root terms of references but now VPN service added which encrypt the connection of the internet by using
doesn’t work on android devices except by using the root terms of references but now VPN service added which encrypt the connection of the internet by using web.
web.
 when your Android device boots
when your Android device boots exit country and IP
exit country and IP
 Everything
Everything

 Tethering
Tethering that it has to pass through the exit node at the specific countries.
that it has to pass through the exit node at the specific countries. it had to bypasses from Exit nodes that exists in the specific countries
it had to bypasses from Exit nodes that exists in the specific countries









